“In Night City, you’re either a gonk or a ghost in the system. Which one are you?” – Hexxed BitHeadz


Jack In
Welcome to this month’s blog, chooms!
Whether you’re a Nomad prowling the city outskirts, a Streetkid hustling the alleys of Heywood, or a Corpo with chrome running through your veins climbing the corporate ladder-you’re gonna want to see this.
In a world where every second counts and every endpoint might be wary, we knew we needed more than just another payload generator. We needed something flashy. Functional. Fun.
Something that felt like a quickhack straight outta Night City.
Introducing: GonkWare! A tool so slick, even a gonk could use it. What’s a gonk? Let’s just say it’s not a compliment.
Now before you acquire this quickhack, we need to make sure your stats are good:

You ready? Let’s get to work!
What is GonkWare?
Well, let’s just say that GonkWare is not a finished product.. is a journey! You will be the Jackie Welles to our V! Your goal is to join us in this multi-phase quest to create the ultimate quickhack. From AES-encrypted shellcode to obfuscated C# payloads, we’re building it all.
Get ready to:
- Generate payloads that drip neon
- Encrypt shellcode with AES-CBC and embed it like a stealth charm
- Inject sleep evasion and obfuscation like a true netrunner
- Package it all up in a glitch-animated GUI with EXE support and auto-MSF handlers
Our fixer Wakako Okada gave us the deets for this job(remember to never ask about her pasts or her dead husbands). Now, let’s get our Jackie Welles cocktail, kick off our Night City op with a banger and get to work. Let’s put Arasaka on a Choke Hold.
The Concept
GonkWare automates a number of steps required to compile custom code prior to target delivery. By release, we wish to support multiple languages, and multiple techniques. This month, we’re showcasing the basic framework and proof of concept. As of today, GonkWare only supports C# languages, and shellcode runner technique.
It’s still early – but it’s working. And we’re hyped to show you.
The GUI
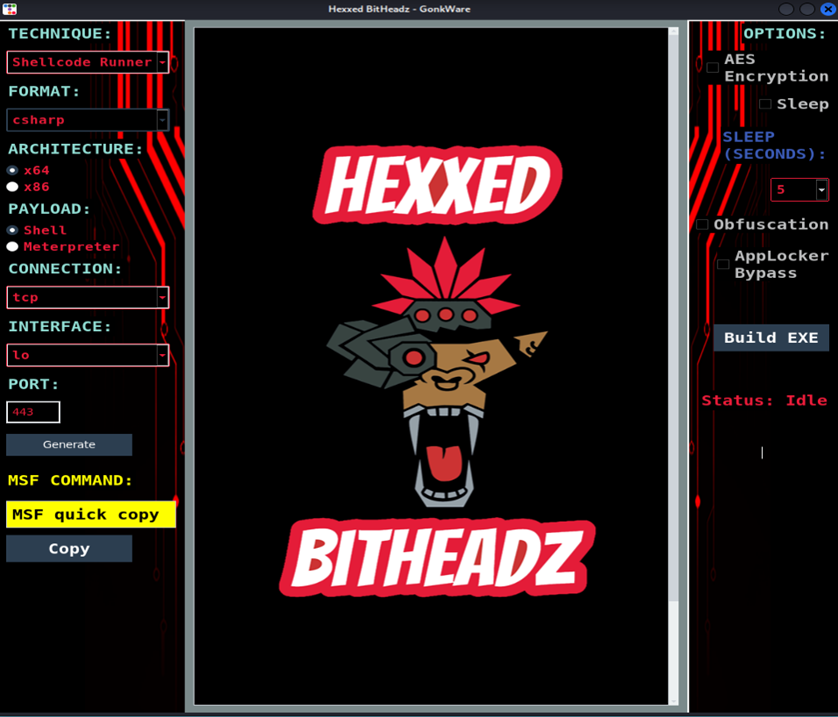
Left Frame
- Technique: Shellcode Runner
- Format: C#
- Arch: x86/x64
- Payload: Shell or Meterpreter
- Connection: TCP, HTTP, HTTPS
- Interface: Whatever interface you need
- Port: Supports all 65535 ports
- Generate: Triggers animated series of Cyberpunk 2077 faction inspired animations while msfvenom builds your shellcode. Then it hands you a one-liner MSF command ready to paste
Center Frame
Displays your custom, ready-to-deploy C# shellcode runner. No high technical level requirements here choom, all that’s next is to move on to the right frame.
Right Frame
- AES: This checkbox encrypts your custom shellcode into AES format, fully equipped with base64 shellcode, key, and iv!
- SLEEP: Add sleep statement to bypass some time-based detections, or something
- OBFUSCATION: Implement junk code, random strings to throw off antivirus << This is an area we want to put a lot of focus into in the near future.
You want to see it in action don’t ya!?
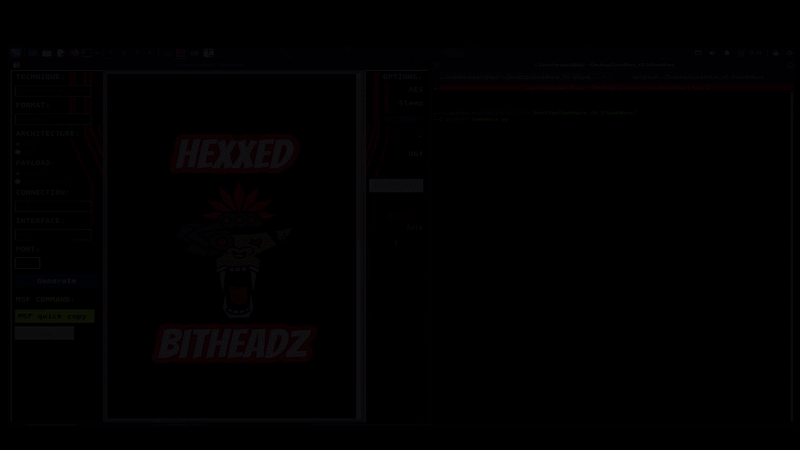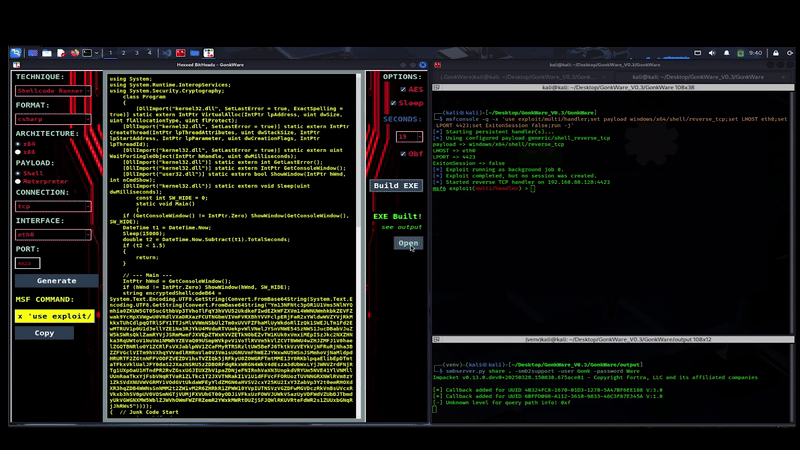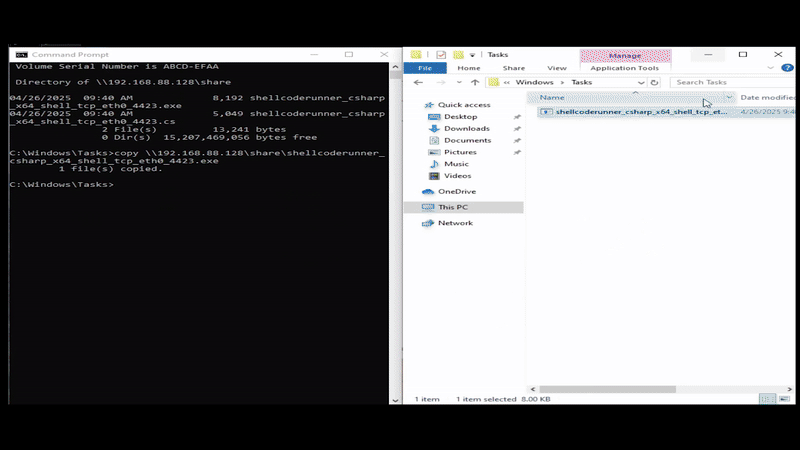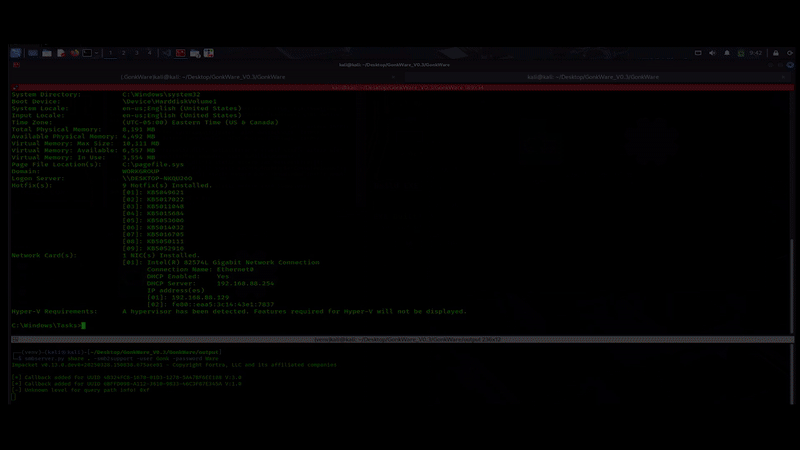
How To Get It:
You can grab GonkWare from directly from our GitHub. We are using a Python virtual enviroment to keep everything clean and avoid Headrush.
You want just the commands.. we got you, choom!
git clone https://github.com/HexxedBitHeadz/GonkWare && cd GonkWare
chmod +x setup.sh
./setup.sh
source .GonkWare/bin/activate
python3 GonkWare.pyNOTE: If you are using Ubuntu, once the setup is finished, make sure to run msfconsole to build the database afterwards to avoid any issues.
The Road Ahead
Most of the improvements planned for next patch include code organization. The code will be broken up into parts. Applock bypass is a feature we are looking to get in right away as well before introducing new formats and techniques. The junk code functionality is also a priority area for improvement. It’s possible we may remove the checkbox for AES and obfuscation in the future, and just have those options automated in, instead of forcing the user to select these obviously desired choices every time.
We feel like it’s worth noting that trying meterpreter payload right off the bat is likely to be unsuccessful at evading defender. Start with shell, get initial access, work your way to a meterpreter shell if desired.
We decided to call this version 0.3, because it feels like it’s about a third of way done before any kind of 1st version release.
TL;DR: Where We’re At
GonkWare v0.3 is live.
Roughly 30% complete.
And ready to evolve.
Stay tuned, chooms -Hexxed BitHeadz
Bonus: What’s Under the Hood?!
Starting with a quick tour of the setup.sh file, first, checking to ensure all the groundwork is already on the host. We’ve only tested our latest versions of Kali and Ubuntu; both seem to be working just fine. First, it’s checking for msfvenom, the core resource for this project. If msfvenom is not found, then the script checks for curl, as curl is needed to download the Metasploit-framework installation. Next, the script is looking for Mono C# compiler. Just as it sounds, this is used to compile the C# source code once the user clicks the “Build EXE” button. I can’t help but wonder if it would be slightly better to go with C++ instead, opening the idea of using GCC instead. Something possibly worth a revisit later on. Python3 venv is next up. Originally the plan was to build GonkWare into a docker container. However, when it came time to build it out, it seemed ridiculous to require the use to download the entire Metasploit-framework into a container, when it’s likely that the user is using a host that already has Metasploit-framework installed. So instead, we decided to go with a checking for a few dependencies on the host, then going with a python virtual environment for GonkWare. Tkinter is next in the script, tkinter is the GUI framework, written in python. Finally, we come to xclip. This is a CLI utility that play a small role in GonkWare. This is what allows the user to copy the dynamically generated msfconsole command once the shell code is generated.
The output is simply where the .cs and .exe files go once “Build EXE” is pressed. Finally, we get to the templates folder. Here is where this all started. The idea was to break up source code into pieces, then build them on the fly, with just a few clicks. Like, build-a-bear, but… with malware. Once we got this to work well with parsed msfvenom shellcode, we were roll’n. While we only see ShellcodeRunner option the GUI, there are other options here in the code, being prepared for future release.
Before getting into the depths of GonkWare.py, a quick stroll through the folders should easily layout the resources. The frameimages directory simply housing 3 png files that give the panes some life. They are fairly basic at this time and hopefully will see some upgrades in the future. The media folder contains several images inspired by Cyberpunk 2077 factions. This is not official art form the game or anything, but generated art to closely represent their cultures. You will only see these images in a glitchy animation while msfvenom generates your shellcode. Feel free to drop your own thumbnails in this folder and watch them glitch out as you hack the planet!
Now, to the main attraction, GonkWare.py. As with any passionate project, it’s funny to see just how fast this tiny python project began to grow. It would be insane to go line by line, so I’ll keep things at a higher level. Right off the bat, we’re handling the GUI stuff. A challenge we have here is understanding how to handle everyone’s screen resolution properly. Right now, we have it so that GonkWare should pop up on the left half of the screen, just slightly shorter than the monitor height. The tricker part seems to be handling the GUI elements, like the labels, checkboxes, dropdowns, etc. We built the app with 1920×1080 in mind and may revisit this topic for more research in the future.
Early in the code, we start defining styles, trying to ensure that cyberpunk palette shows strong. The frame images get loaded in then the individual elements spawn in. The user simply selects their options, enters the desired port number, then generates the executable. So easy, a gonk could do it! The entire left pane was pretty straightforward, it was the right pane that was difficult to get working the way we wanted. Getting the checkboxes to play nice with each other when checking / unchecking took some tries but seems to be working as intended. We are happy with the AES encryption and sleep functions; those seem to be in great shape. While the obfuscation function does put in some junk variables and functions, we feel like there’s a lot more work to be done here to really junk up the code and misdirect AV software. Once we get obfuscation in a better place, we would love to implement applocker bypass functionality as well.
So finally once all the options are selected from the left and right panes, the user clicks the “Build EXE” button, mcs will compile to an exe within the output folder, ready for delivery. There’s even a .cs file that generates, in case it can be used or modified by the user. It’s probably safe to say that 90% of the python code is building the GUI, loading the images, doing the animations and such, while very little of it is actually doing the behind-the-scenes shellcode-to-C# and compiling.
You made it this far, good!