It was only months ago we got to go do our very first cyber related talk at BSides Las Vegas, which involved demoing how a malicious DLL mod for Skyrim could look like. At the end, during Q&A, someone asked a question along the lines of “How many corporate computers do think have Skyrim installed?”
I think it was asked kind of intended as a joke, we laughed about it, agreed that well, probably not many high value assets have a copy of Skyrim on it, it made me wonder if maybe there’s an opportunity to show off a malicious DLL in a different perspective.
Ever since that question in Vegas, it’s kind of stuck in the back of my head, like, what else can I use to demonstrate this attack vector that is not a video game. Maybe some software that is potentially installed in a different environment? I needed something that works in that similar process. Something able to load a DLL as a mod… or…. plugin rather…
It didn’t take long to discover Notepad++ was perfect for this month’s project. It’s not a video game, it’s possibly more widely used across environments other than home gaming machines and it supports plugins via DLL. I know, I know, if you’re like me, right now you’re thinking… Not Notepad++! Leave this beautiful, perfect piece of software alone, you old, bored bastard! However, I couldn’t ask for much of a better proof of concept. In fact, there’s even a Notepad++ plugin template to get my new malicious plugin experiment rolling.
I plan to loosely follow steps used before, learning how to build a very basic plugin, learn how to execute local code execution to pop calculator, then build shell-code into the source code, compile it, slap in the right directory, and call back to a listener. If all goes well, might as well slap in a Havoc C2 callback… Ya know, for more of them lulz!
Before continuing, I want to clearly call out that this is not a vulnerability in Notepad++. In fact, whenever trying to copy an file into Notepad++’s directory, malicious or not, a message box does pop up requiring admin privileges, which is what should happen. To clarify, this is more of a “DLL exploration” blog entry, and not a “Notepad++ vulnerability” blog entry.
GETTING STARTED
As previously mentioned, there’s a template out there to use that has pretty much everything set up, found here:
https://github.com/npp-plugins/plugintemplate/releases
I opened “\plugintemplate-4.4\plugintemplate-4.4\vs.proj\NppPluginTemplate.vcxproj” in Visual Studio 2022 Community to get started. I followed the code a bit, tried to get a feel for where I needed to begin my new adventure. It all came down to PluginDefinition.cpp, hello() and helloDlg() functions.
The helloDlg() function jumped out to me as the perfect spot, as the existing code populates a dialog box when ran, making troubleshooting a little easier moving forward. Now, the strategy begins, I wanted to see if I could get local code execution by getting the calculator application to execute from the plugin template.
CALC POC
https://github.com/HexxedBitHeadz/NppDLL/blob/main/PluginDefinition-1calc.cpp
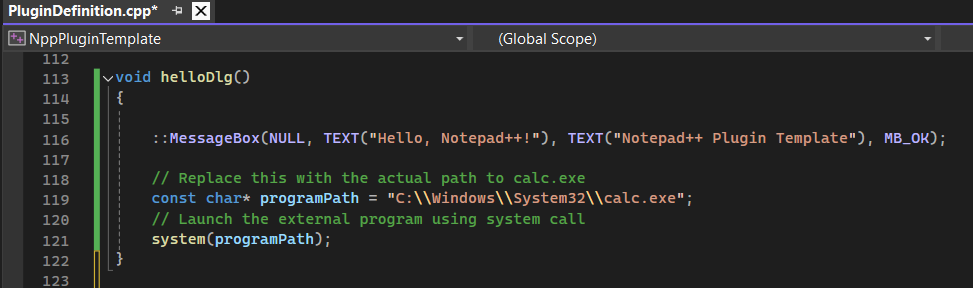
The instructions mentioned that I would need a folder within the Notepad++ plugin folder with my plugin name, so for example:
“C:\Program Files\Notepad++\plugins\NppPluginTemplate”
Where “NppPluginTemplate” will be the folder where my compiled DLLs will live. Again, this is where the administrator permissions pop up will occur. IF this didn’t occur, this would be considered a vulnerability, as it would be much easier to take advantage of unsuspecting victim. Can one still have this delivered in a trustworthy disguise? Possibly, just like how Skyrim has Nexus mods, Notepad++ has a plugin catalog. If a well disguised malicious plugin made its way there, it could be successfully deployed. Stretch? Yes. Possible? Why not?
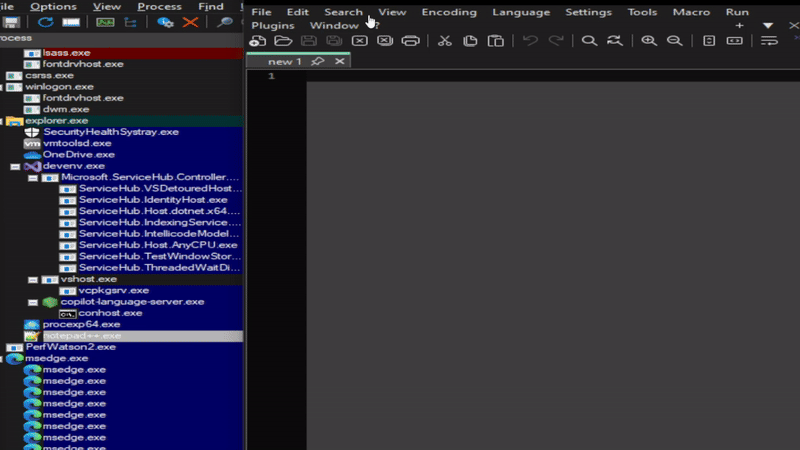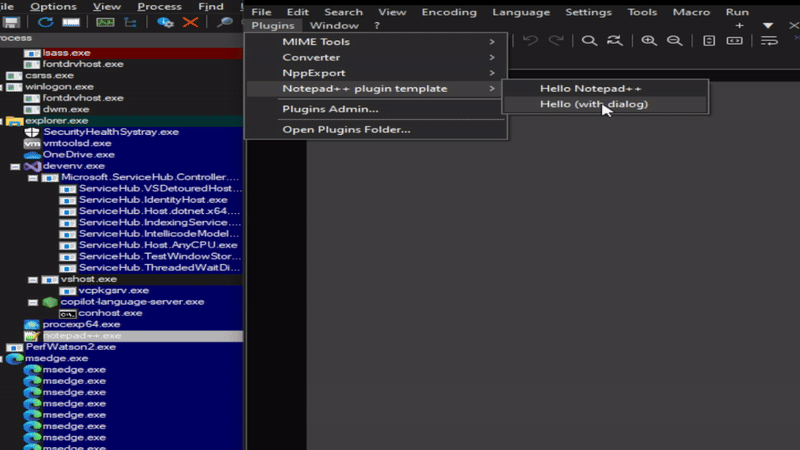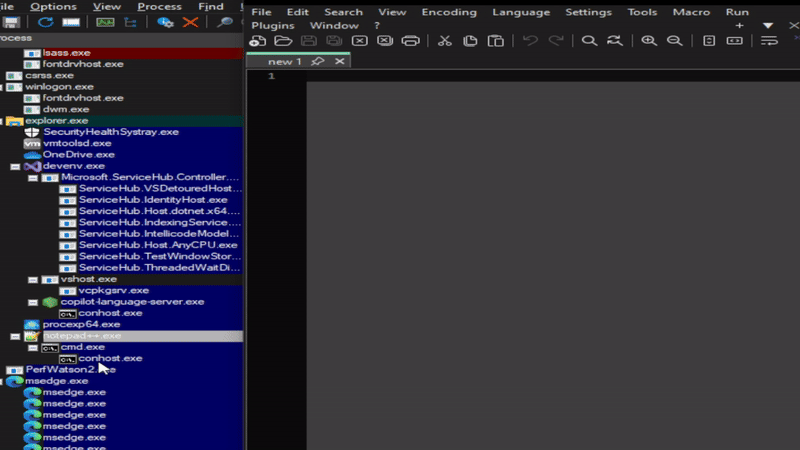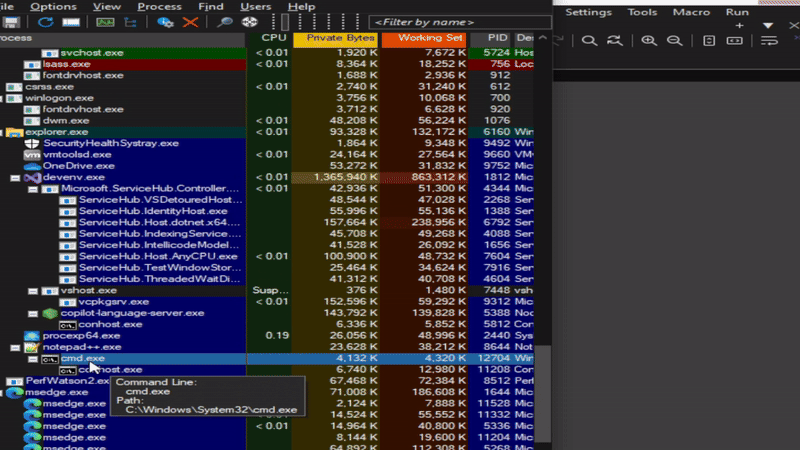
Ready for the first test, I fire up Notepad++, go to the plugin menu and launch the new Notepad++ plugin template option selected the 2nd option, hello (with dialog), first get the dialog box popup (Hello, Notepad++!), click OK and calculator loads!
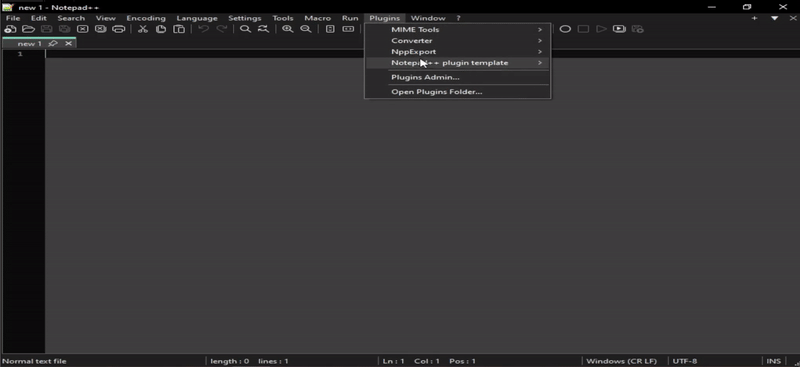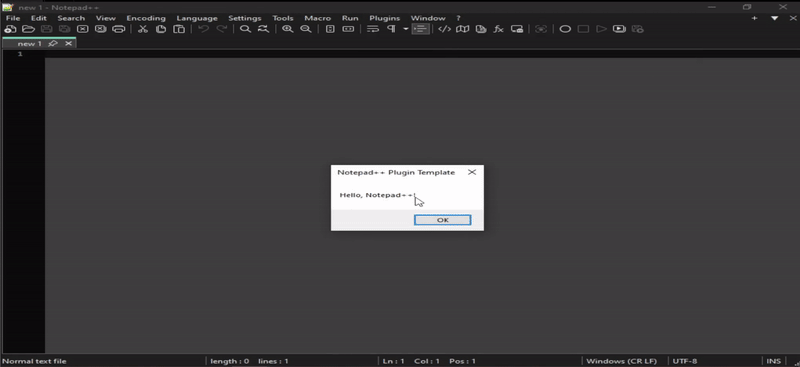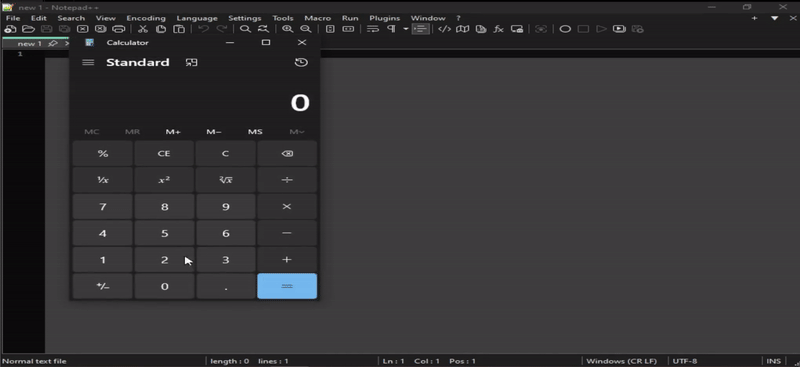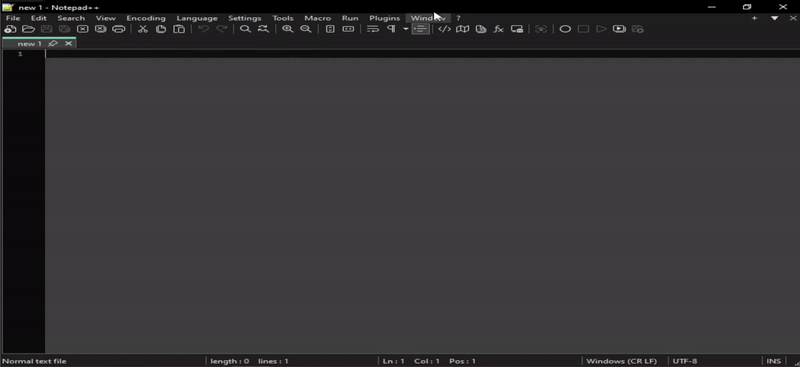
I gave myself a proper “HELL YEAH!” alone in my office…

REVERSE SHELL CPP
https://github.com/HexxedBitHeadz/NppDLL/blob/main/PluginDefinition-2revshell.cpp
I was feeling as cool as Stone Cold Steve Austin in a sad empty arena. I thought for sure all I had to do was duplicate the reverse shell source code from the old Skyrim project, and it would all just… work. I was like “yo, I’m gonna knock this out sooo fast”. I copy / pasted like a pro, only to see Visual Studio IDE lite up with errors like a friggin Christmas tree. As if taunting me, each red squiggly line thrown in my face for thinking I was that knowledgeable of a malicious programmer. Did I lose that Stone Cold coolness? Did I freak out and panic? I did, I did a little bit.

After spending way too much time trying to work my way through each and every error, only for new errors to appear out of nowhere, the only logical path forward was to blow up the whole source code, and figure out how to mimic the old project, step by step, executing in a new way. I was able to branch off a new thread function called runInteractiveShell(), and get a call back to my listener! The shell was a bit wonky, it would sometimes not take my commands, or be one behind, I would have to enter commands twice. I got it improved a bit; the commands execute as expected, just have to hit enter twice to send out. To get into the weeds a bit, a couple different libraries got swapped out, while still using winsock2, I have discovered the usage of recommended InetPton over the now out-dated inet_addr.
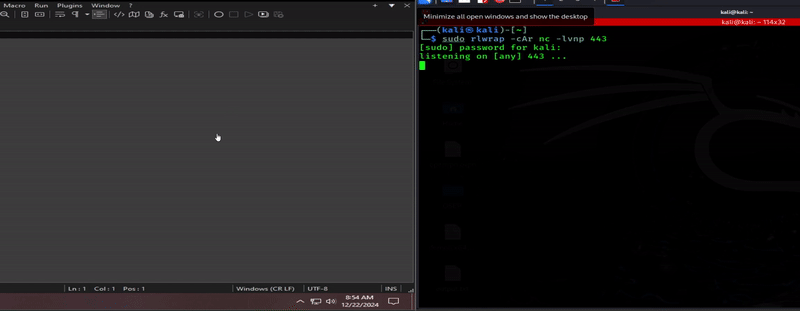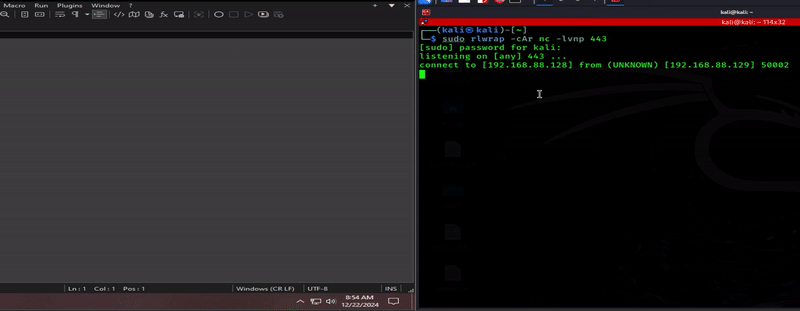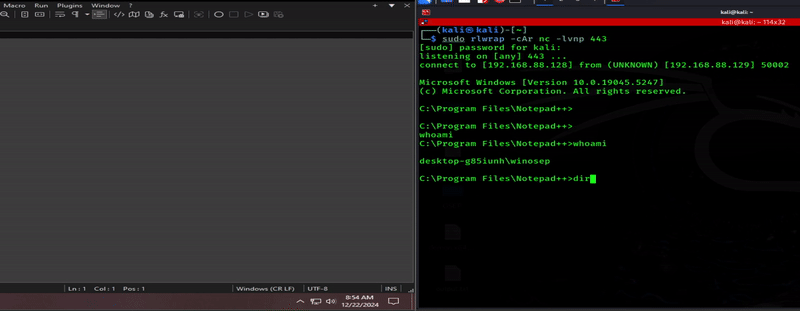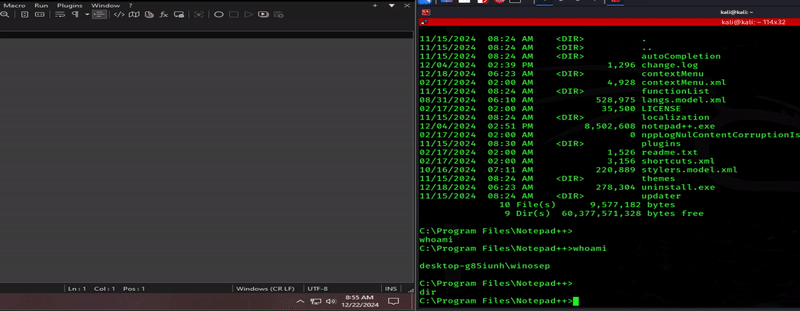
BOOM! Gave those error squiggles the Stone Cold Stunner!

Maybe not the best form, but I imagine that’s about what my Stone Cold Stunner would look like.
REVERSE SHELL MSFVENOM
https://github.com/HexxedBitHeadz/NppDLL/blob/main/PluginDefinition-3revshell-msfvenom.cpp
After getting a solid shell working, I was really interested in getting shell-code execution implemented to the source code. Luckily, the adjustments needed to make this happen were easier than that previous reverse shell example. Quickly generating shell-code with msfvenom, throwing it in the POC and execute, I get a much more stable shell back that works flawlessly.
Was curious how this looked in Process Explorer, so decided to take a look:
HAVOC C2
https://github.com/HexxedBitHeadz/NppDLL/blob/main/PluginDefinition-4Havoc.cpp
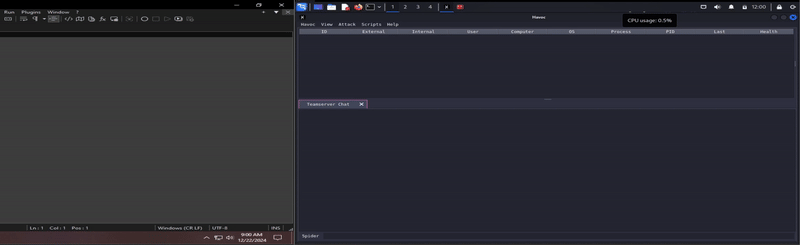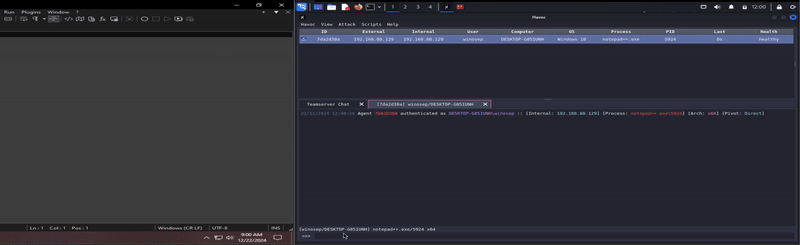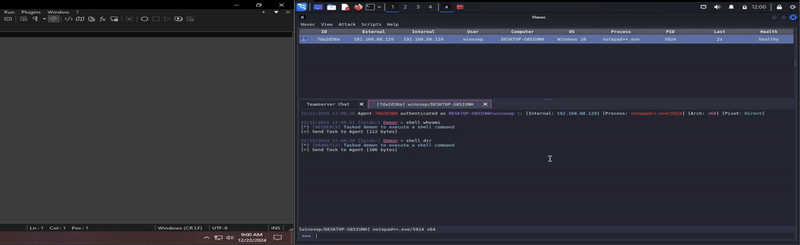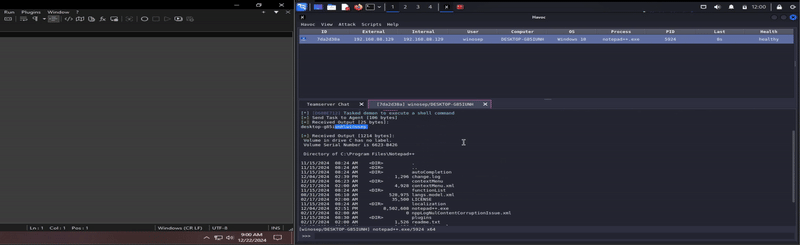
Well I got this far, why not look at executing a C2 beacon from Havoc from this plugin? This worked out exactly as before, generate a bin file from Havoc, using xxd to generate the needed shell-code, slap it in the source code, build DLL and execute.

VITA
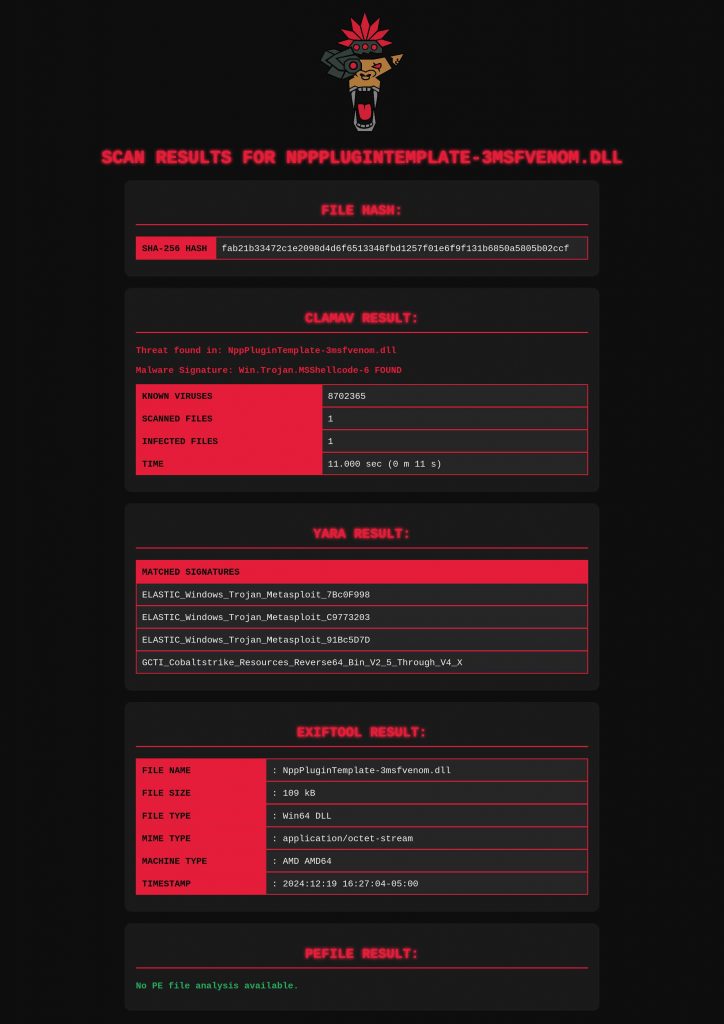
Our November blog consisted of putting together a local file analysis tool that uses clamav, yara rules and exiftool to generate a report of findings. VITA can use some more resources, as it’s definitely not comparable to something like VirusTotal or antiscan.me, but I thought it’d be worth uploading the four DLLs generated from this project to examine the results. The most interesting file ended up being the msfvenom shellcode generated DLL seen below:
Wazuh
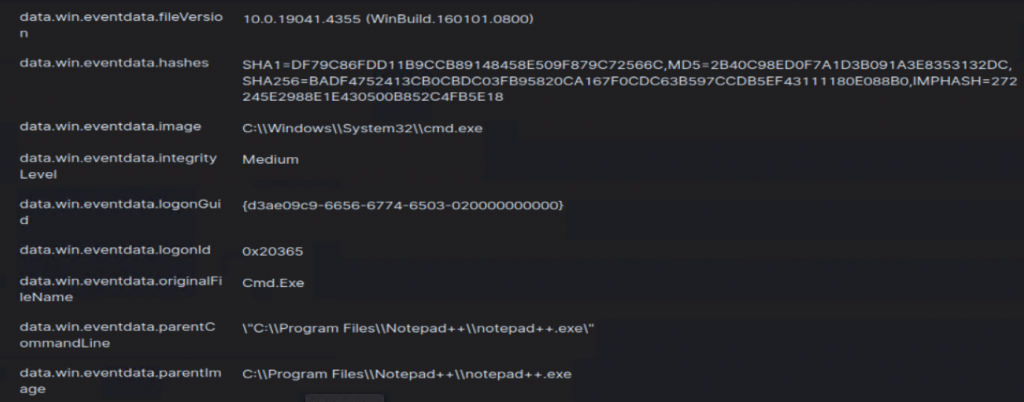
Ok last thing, I swear. Awhile ago, I did a Wazuh set up, and wanted to throw reverse shell cpp version of the plugin on a Windows host that has a Wazuh agent on it, see what Wazuh thinks about my Notepad++ hack-tivites.
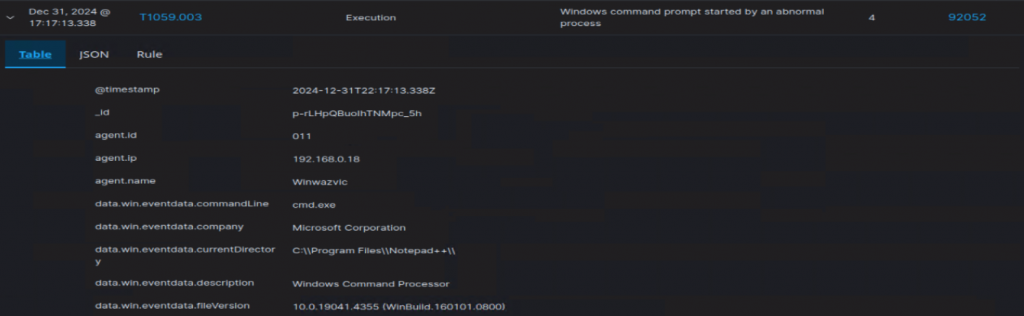
DAMN! It got me! lol. It was logged, however the integrity was labeled as medium, which I can’t help but wonder, if it were me monitoring activities such as this, would I think anything malicious of this? Or would I simply think to myself that this program is running it’s update executable (GUP.exe in the update folder, for example).
That’s a wrap from me this month! Hope your New Year is starting off well! Till next time.

