I don’t know who the hell started this “themed GIFs” thing in our blogs, but I’m pretty sure it was Izzny. If it was indeed me, I’m still pointing at Izzny. I didn’t have a great GIF theme idea for this one right away, but I also didn’t want to be the one to ruin this trend. I soon discovered Super Troopers was perfect for this one. For this month, I am revisiting my VITA tool, looking to… enhance it.

Hell yea, see what I did there!
Awhile ago I was going through this malware course from crackinglessons.com. As I was going through the beginner, level 1 material, I kind of wanted a way to analyze these files we are creating through different tools. While these are basic malware samples, I was curious to see how some software detects and categorizes these files. Also, this could be a good reality check, since it can scan my compiled (potentially) evasive, incredibly well written malware, and have this tool destroy all my confidence by calling out every method it found within a nicely formatted report, with my own logo heading the page, illuminating that good ol “try harder” vibe.

You see meow, when I did the original VITA blog back in November, I had this dumb setup where the tools were spread across multiple raspberry pis, and they would work together to perform the scans and generate the report. It had nothing to do with efficiency, I just needed to justify to myself that I needed FOUR raspberry pis.

I have meow consolidated VITA to needing just ONE host. Even better, VITA comes with a dockerfile, making it easy to obtain and install containerized. So, what I want to do with this is very similar to November’s blog, I’m going to generate some malicious files, run them through VITA, and showcase what’s new, all while slamming back A LITER OF COLA.

VITA can be found here: VITA
The file structure once downloaded will look like this:
/VITA
├── app.py
├── Dockerfile
├── static
│ └── HexxedBitHeadz-Logo.png
├── templates
│ ├── upload.html
│ └── results.htmlINSTALLATION STEPS
git clone https://github.com/HexxedBitHeadz/VITA && cd VITAsudo apt update && sudo apt install -y docker.iosudo docker build -t vita .sudo docker run --rm -p 5000:5000 --name vita vita
WHAT’S NEW
A bit snazzier upload interface, meow with Drag and Drop feature. Nifty “Analyzing File” progress bar. Capa by fireeye implementation, oletools to test Microsoft Office supported files.
TEST RUNS
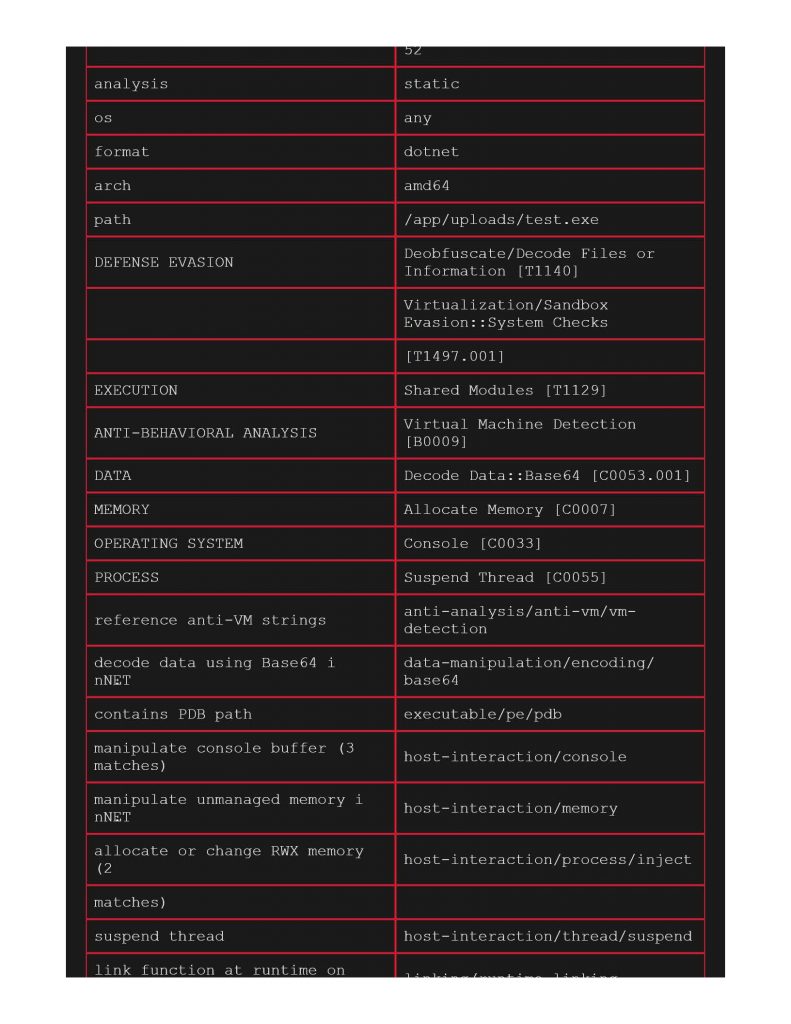
Taking several examples from the beginner section, compiling through Visual Studio and uploading the produced exe / dll files through VITA, I was able to meow get a sense of how some tools worked. I gotta hand it to capa, it did an incredible job calling out the capabilities of the files thrown at it. ClamAV picked up a few things, and Yara flagged a few for Metasploit stuff.
RESULTS
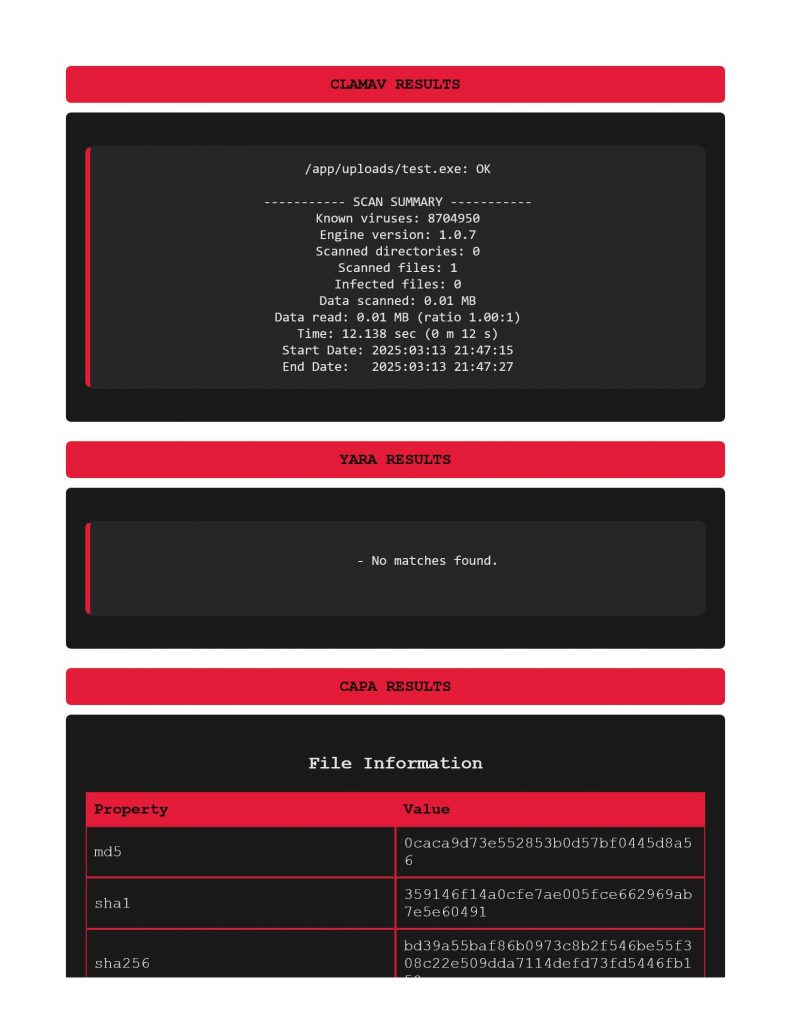
Starting with a file with aes encryption shellcode, we see in VITA that ClamAV did not find anything considered “infectious” on this file, and no Yara matches. Within capa on page 2 however, it did call out AES encryption.
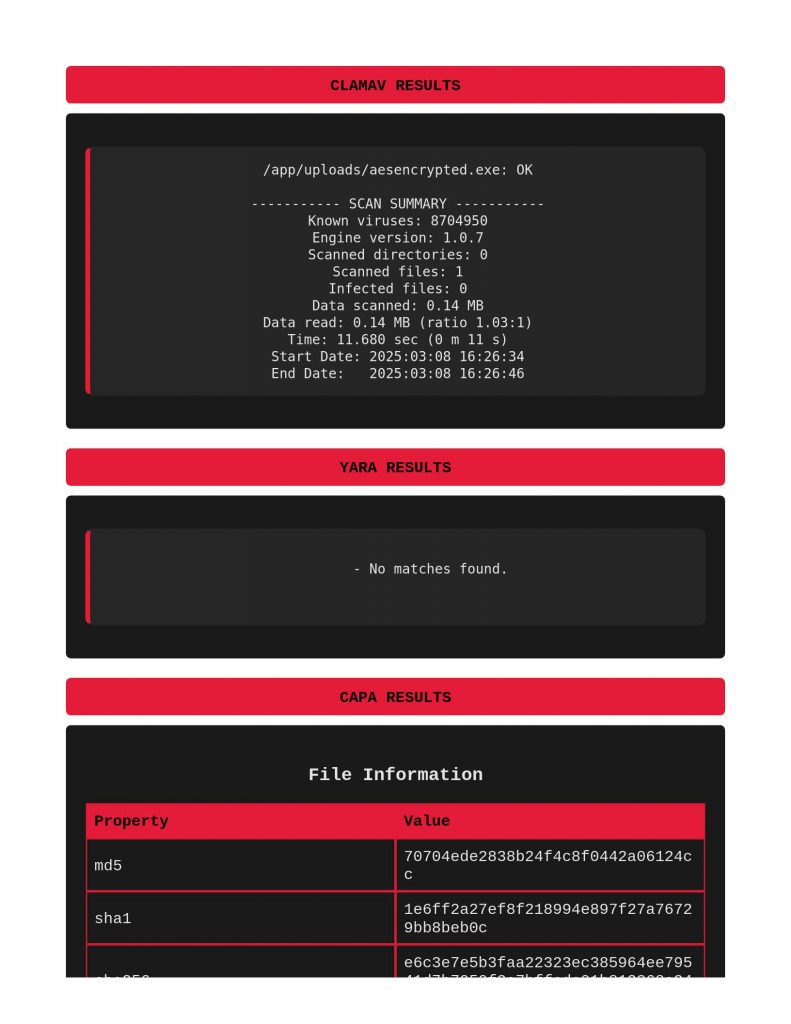
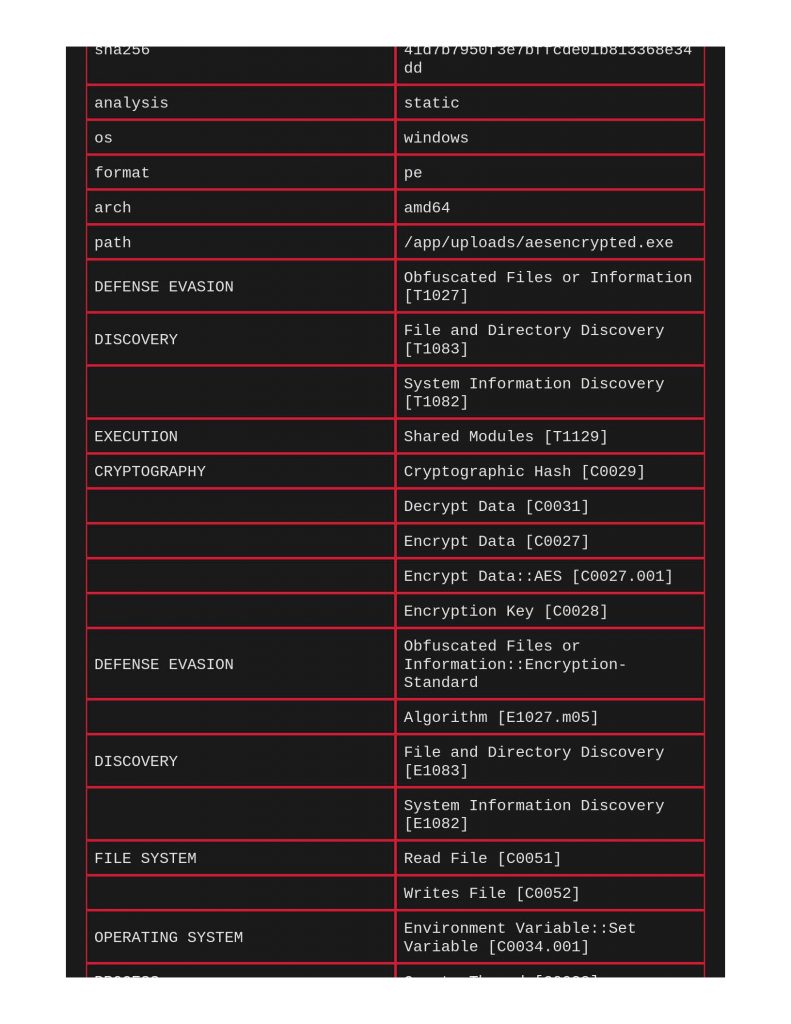
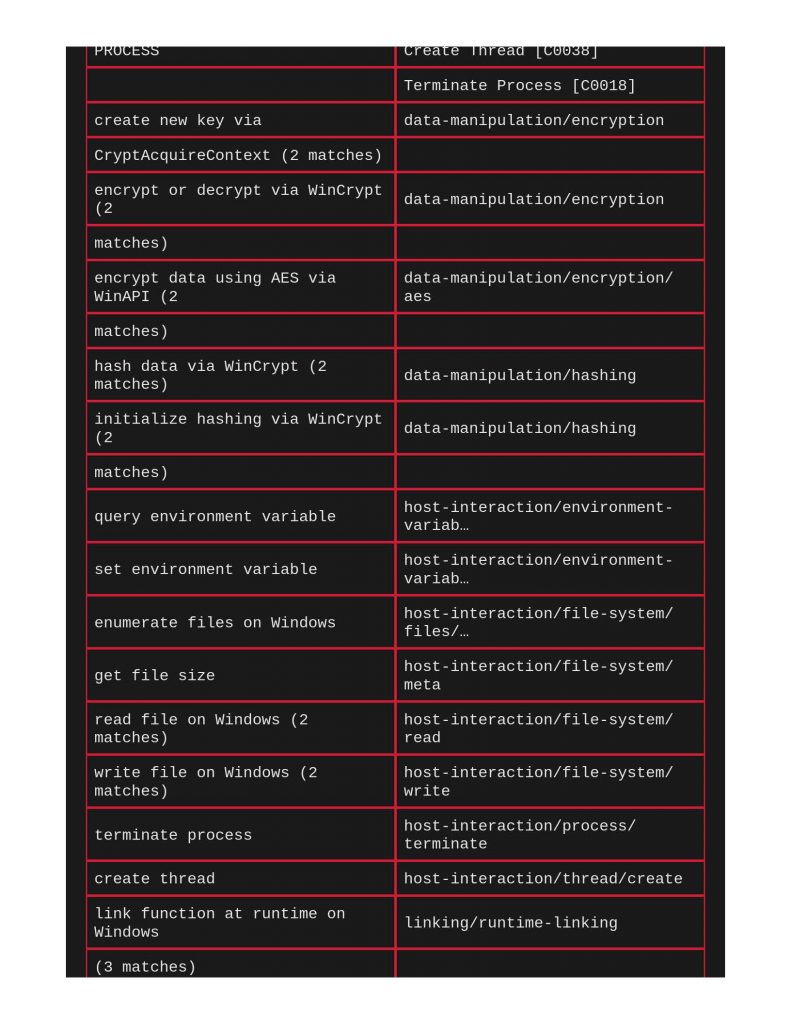

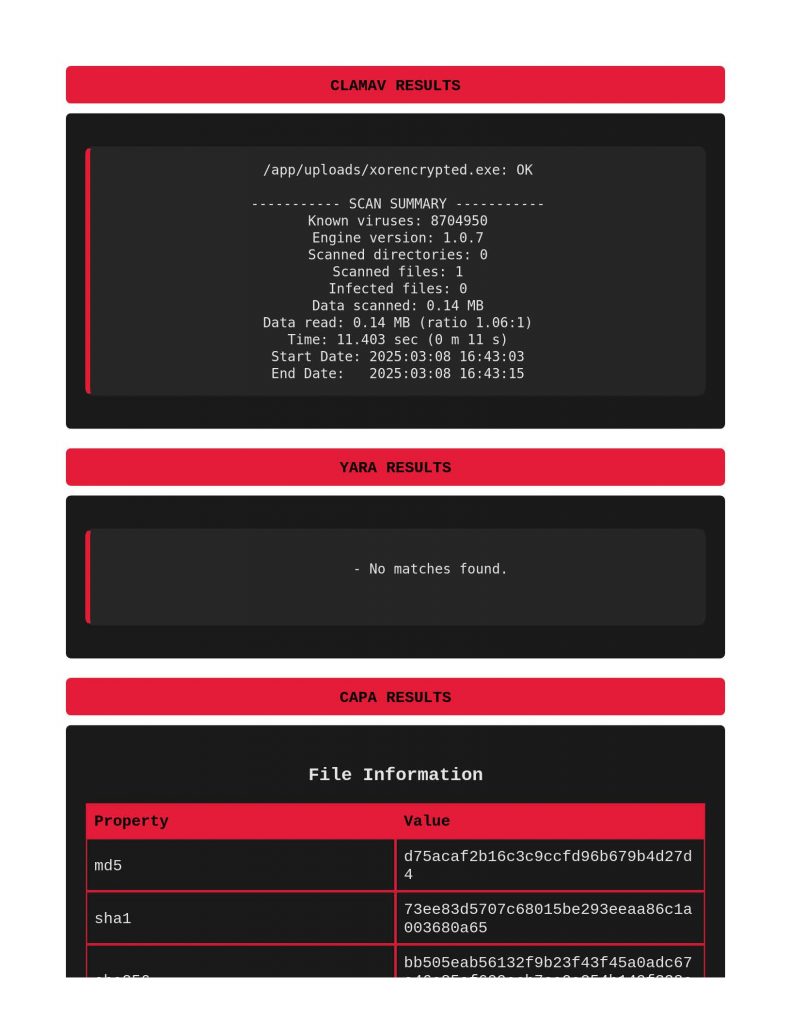
Next, taking a look at xor encryption. Same thing with ClamAV and Yara, capa does indeed call out the xor encryption being used.
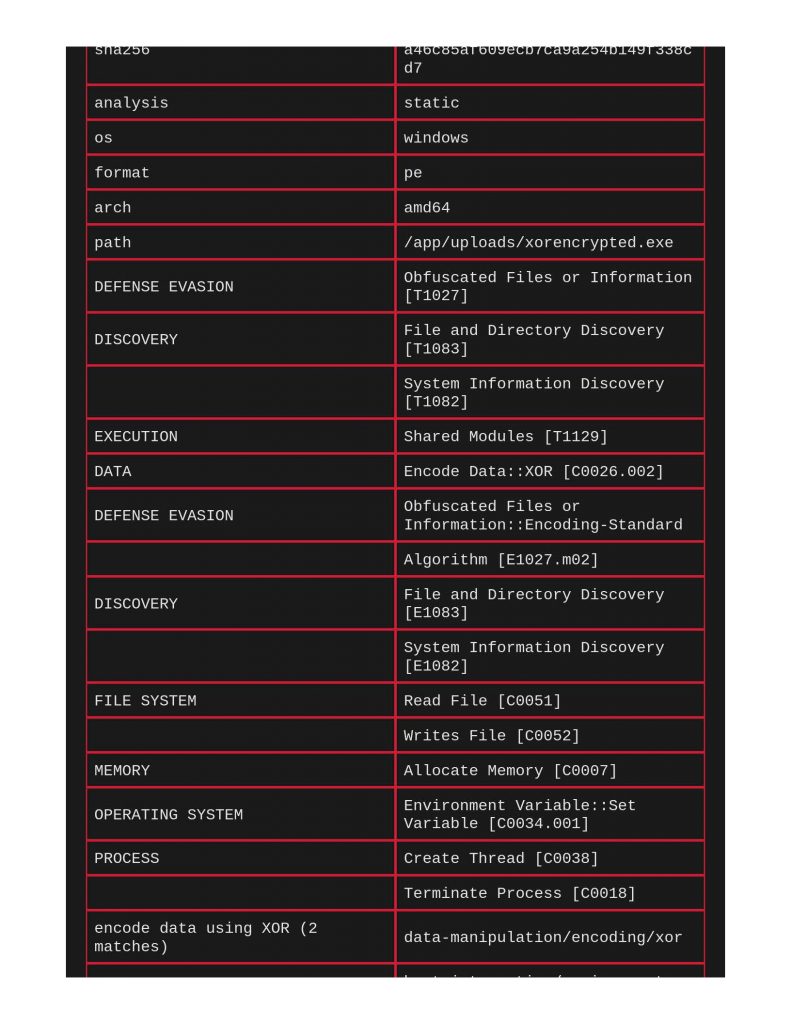
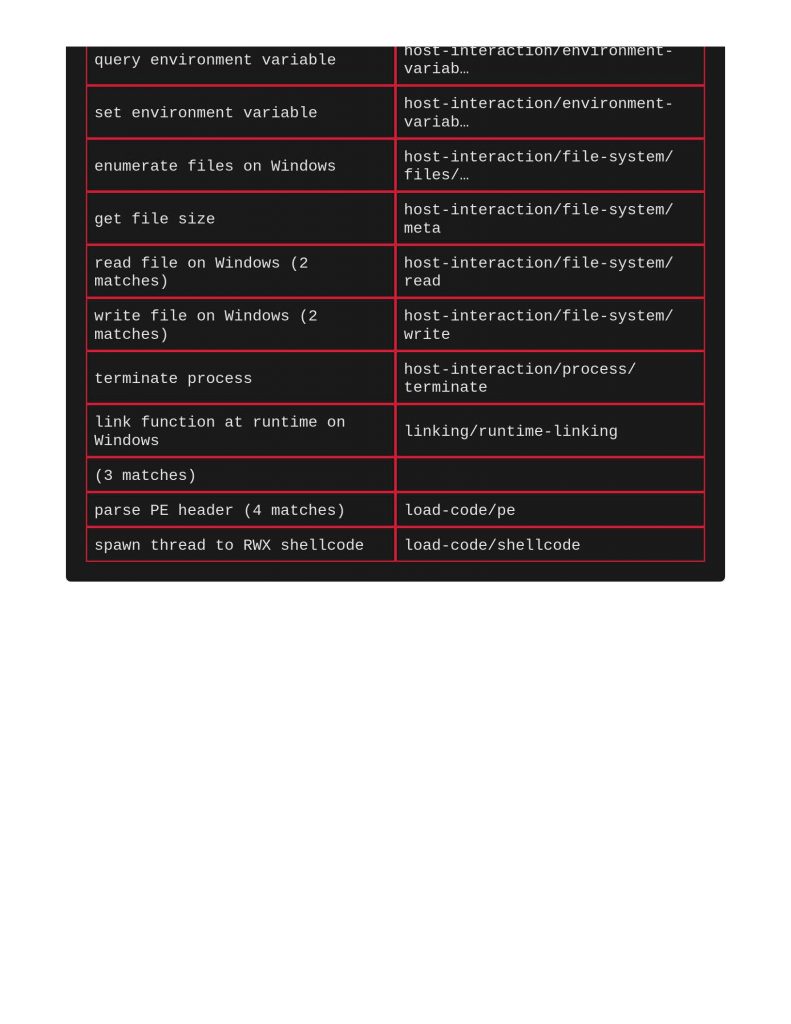
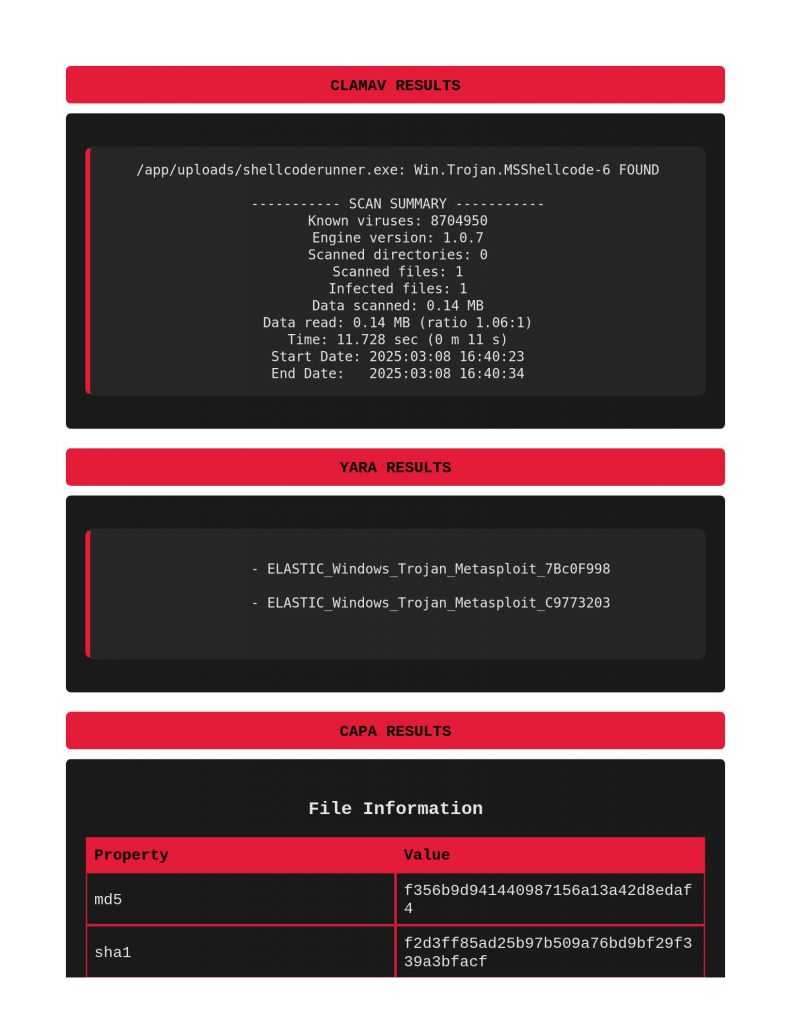
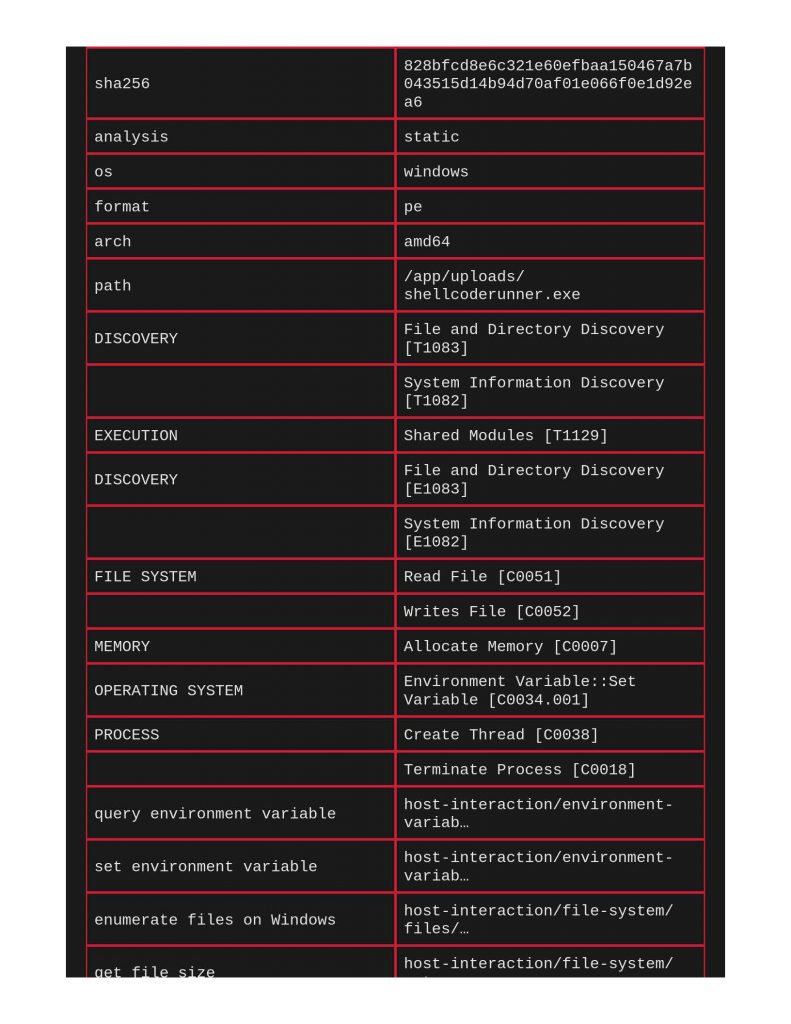
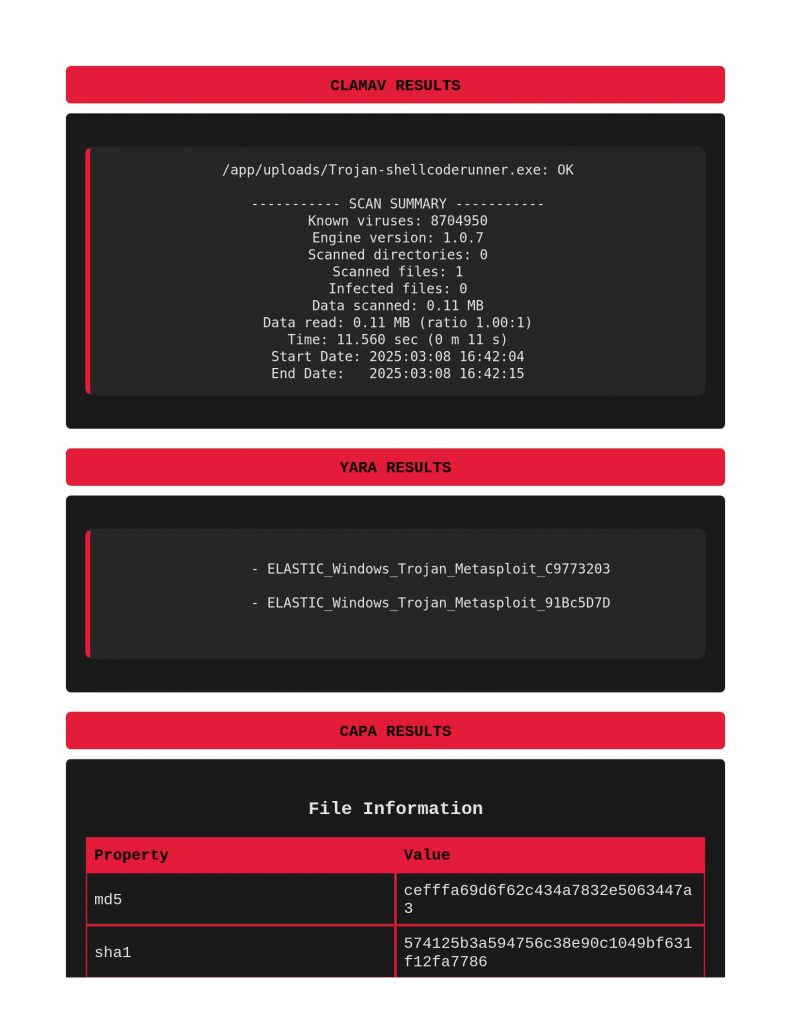
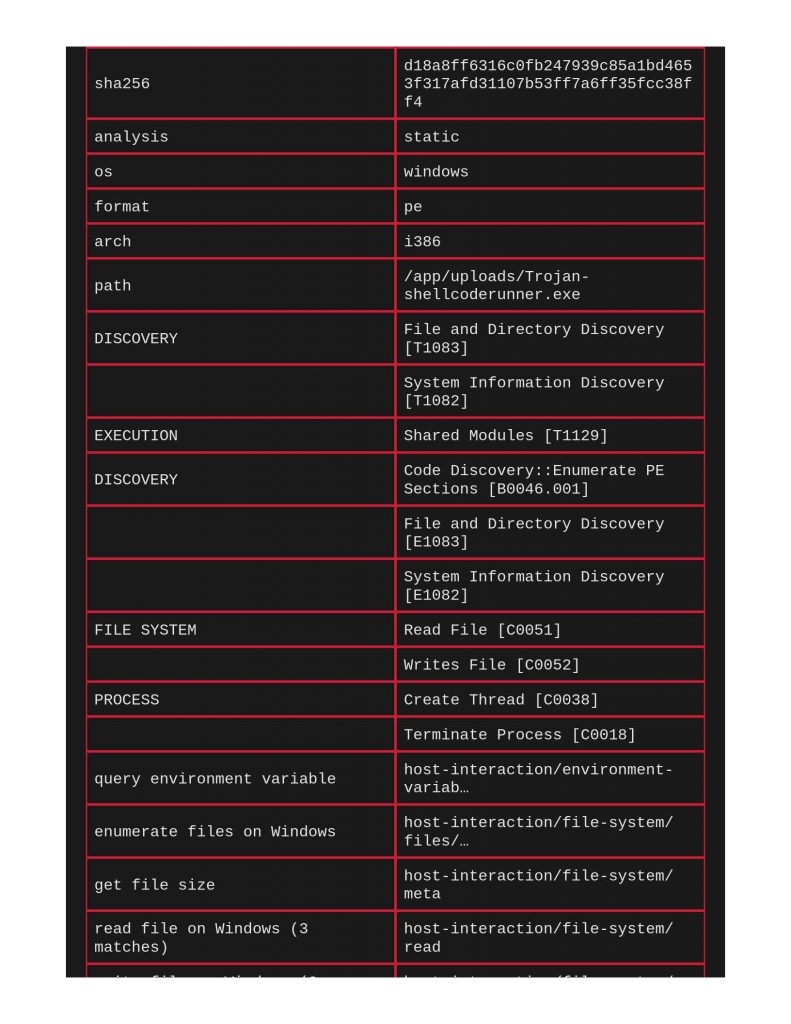
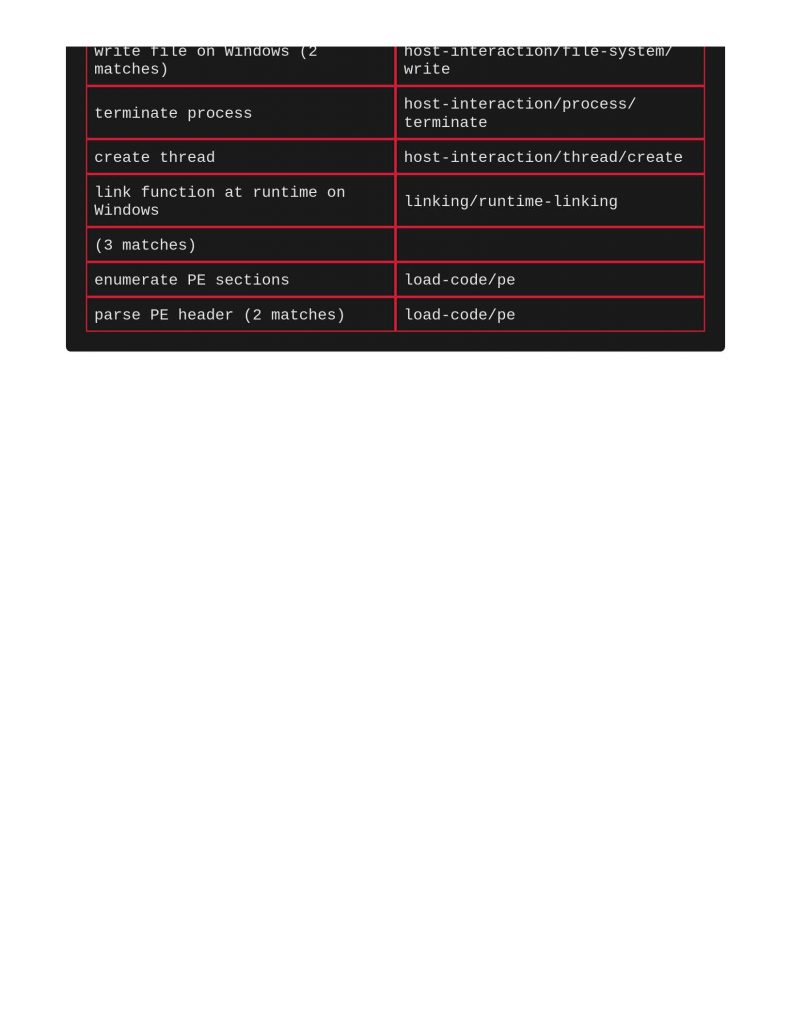
Next file to scan was a shellcode runner. Notice below that ClamAV and Yara did actually call this out for identifying Windows Trojan Metasploit Shellcode. Capa really does a great job meow calling out file’s capabilities and TTPs.
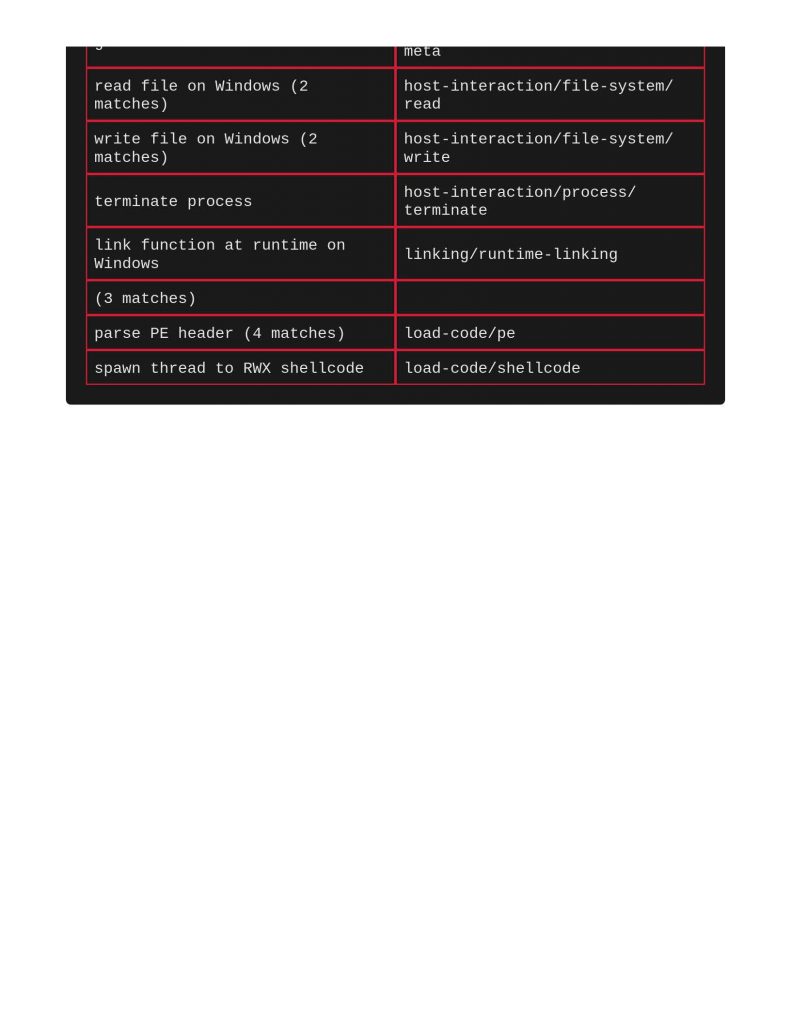
Next example is a Trojan, not flagged by ClamAV, yet was definitely called out by Yara, meow that’s interesting!
Process Injection results were fun to review, notice below that nothing came from ClamAV or Yara, but capa noted under the DEFENSE EVASION row that process ejection techniques were found.
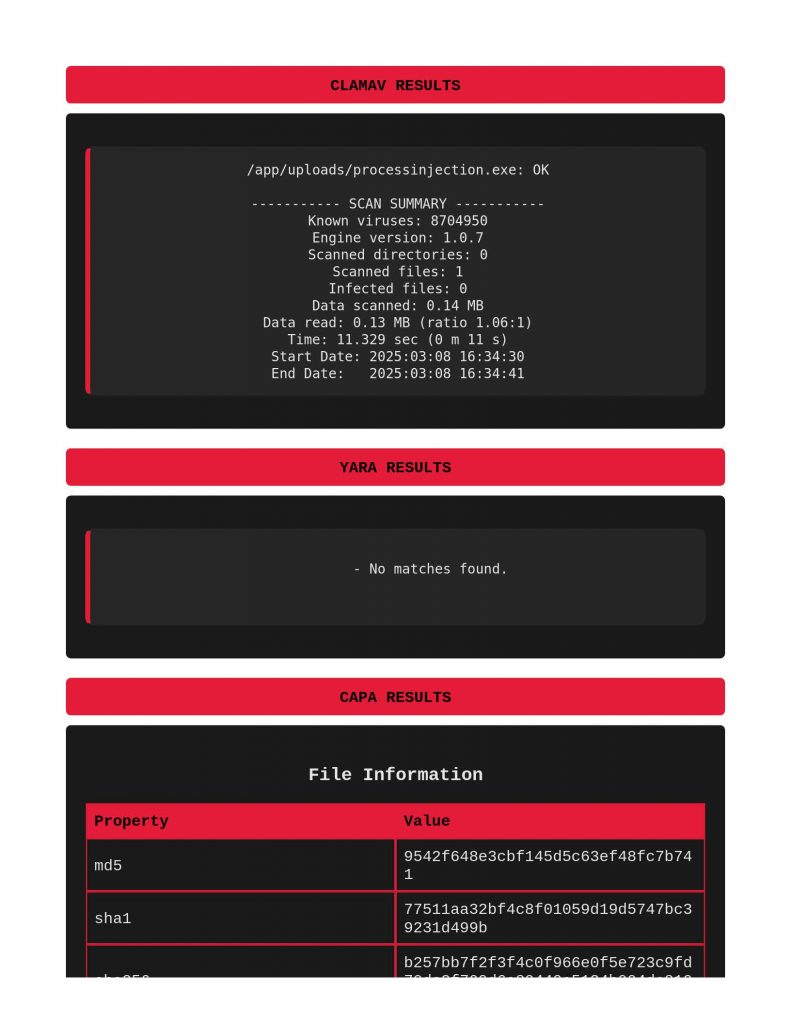
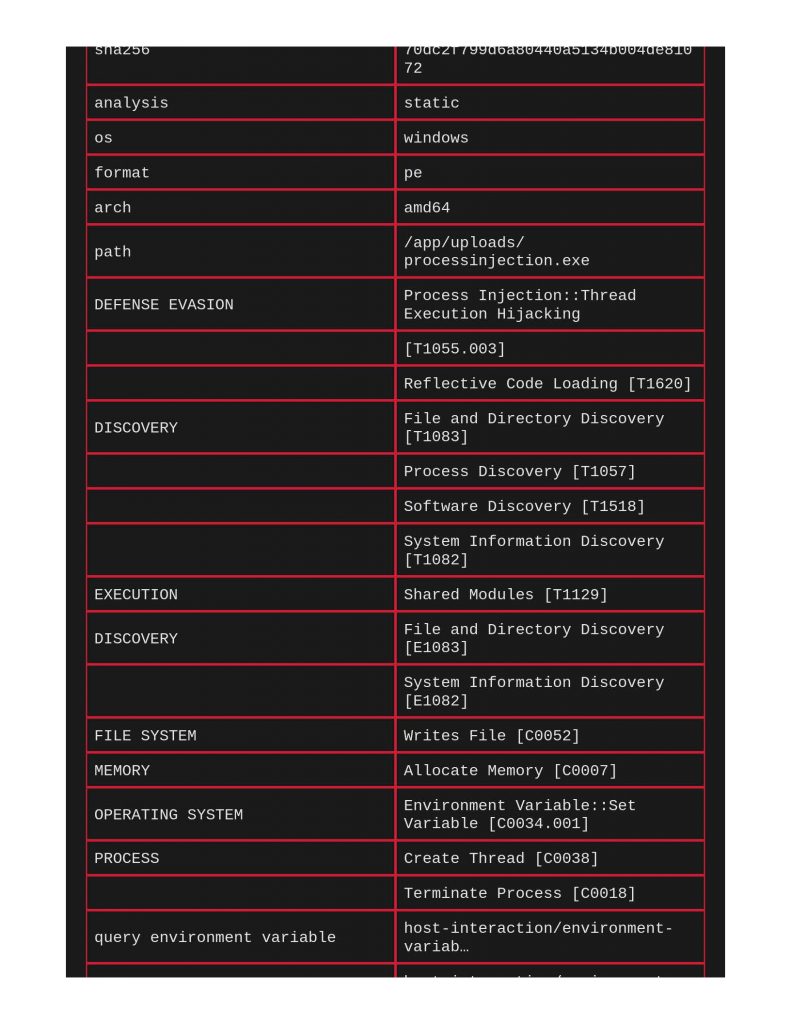
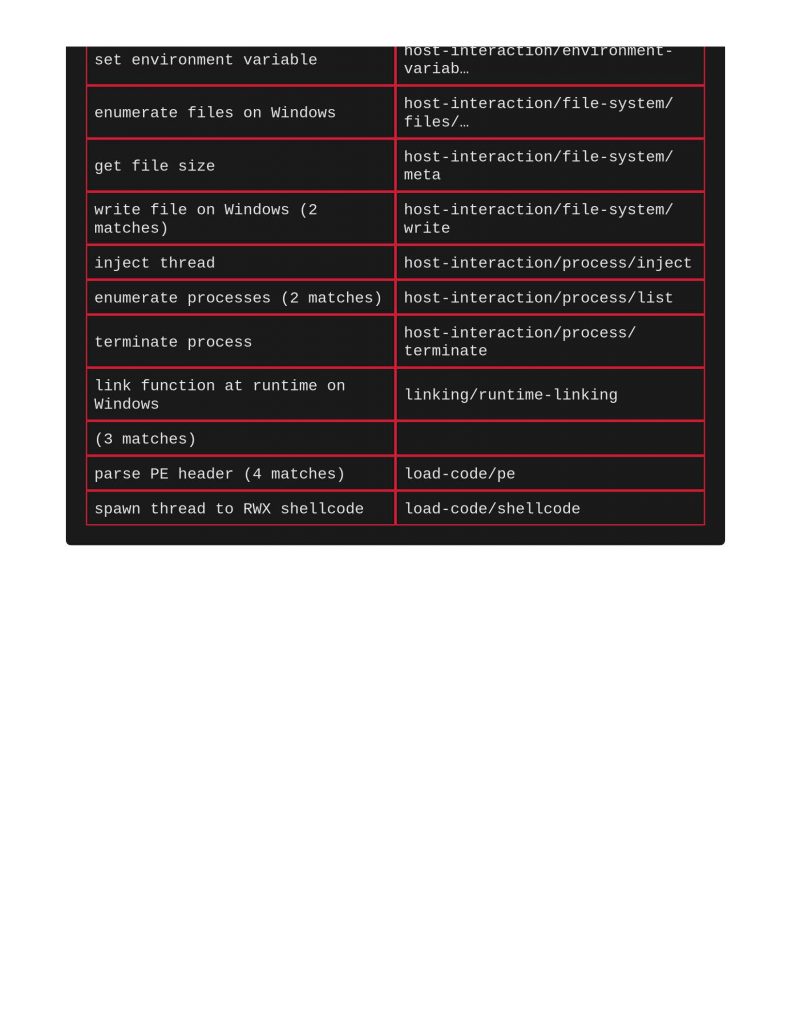
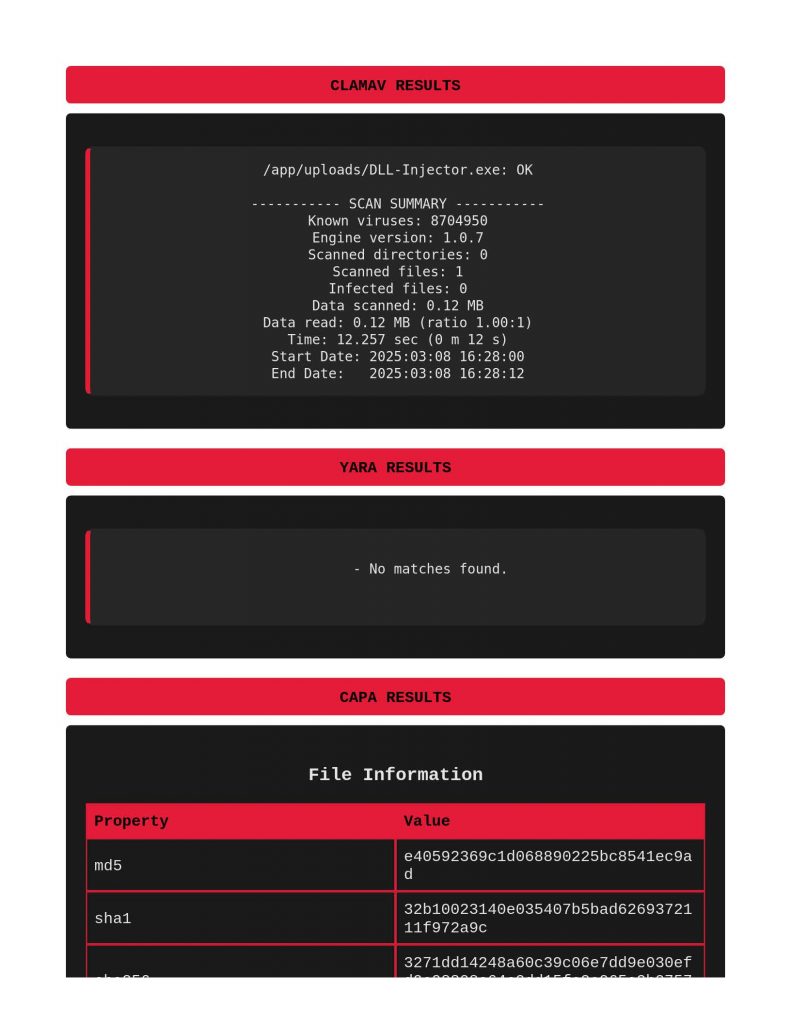
Giving it a basic DLL injection sample, nothing from Clamav or Yara, again though, capa successfully calling it out in the DEFENSE EVASION section.
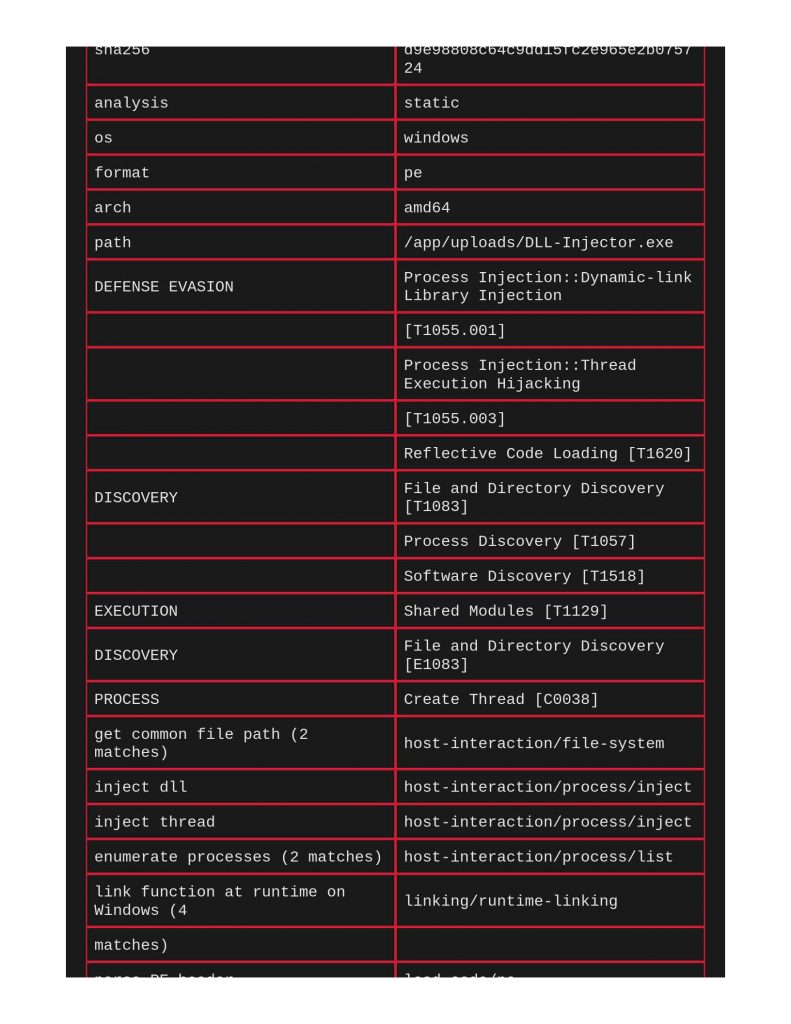

That’s all the executable files I tested, but since oletools have meow been built into VITA, why not try a word doc with a malicious macro? Of course, oletools was able to sniff out the vba code and label it malicious. Pretty awesome.
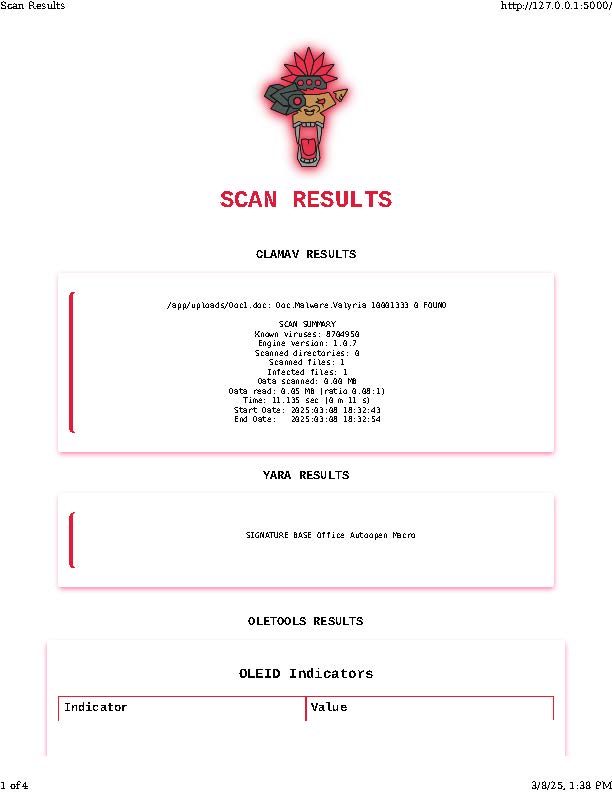
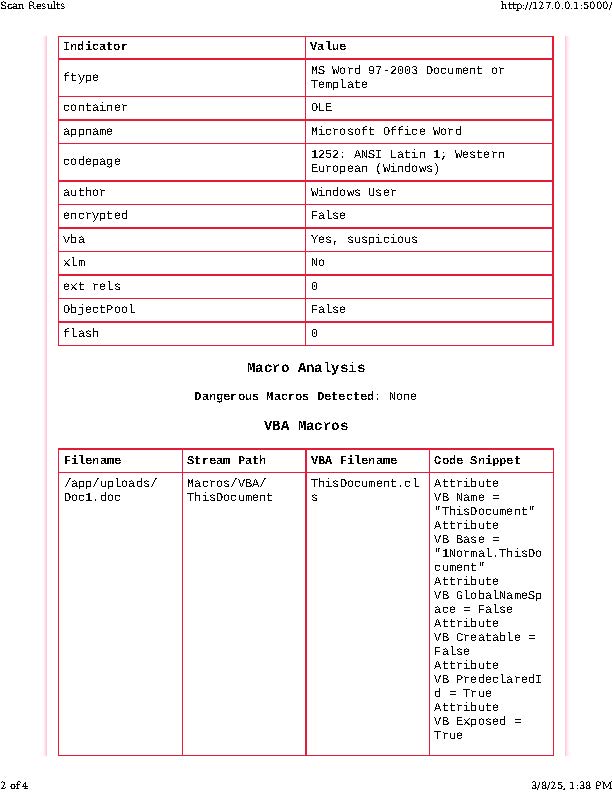
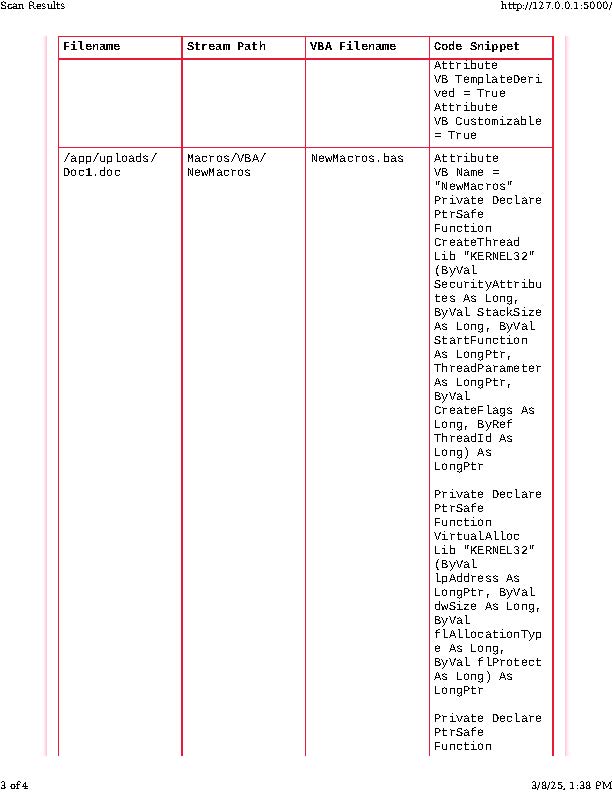

Okay, I totally lied and snuck in 1 last scan at the very end. Over the last few weeks, my focus has been more towards further obfuscation of malicious code, better encryption techniques, AppLocker / CLM bypass.
CONCLUSION
So, did I manage to make VITA everything I’ve dreamed of after round 2? Still no, and I have to accept the fact that this feels more like a Blue Team / Post exploitation resource than some kind of malware testing development resource. I also have to admit, I put a smidge to much confidence in how ClamAV works for this kind of experiment. That or I just straight up misused it. Either way, it sure felt like the antivirus engine was too busy chugging syrup to keep up.

It was fun to revisit, reformat VITA into a Dockerfile setup, and try some new things. Ultimately, the result is obvious, when trying to test against a specific detection engine, nothing beats testing against… that detection engine. Who would have ever imagined!?

Farewell data dwellers, I’m off to new shenanigans meow!


